Defender for Cloud Apps – Client-certificate auth

In this week’s post, I want to address the following question – Can I have access control for some vendors that cannot register their computers to my Azure AD tenant? They need to access my Azure Portal to manage some virtual machines and other activities, but I won’t join their devices or even use Intune in this case.
So, the first thing we could use is a virtual machine acting as a jump host for this type of access using a solution like Windows 365. Then, we could harden this VM and set some additional controls. But this was not an option for this project.
In this scenario, I already have the same controls for internal workstations and admins but using Conditional Access, Intune, and other controls such as PIM (Privileged Identity Management) and Identity Protection, since they have admin access to the environment.
We have another possibility for a scenario like that, and I want to present it today. We can leverage the same Conditional Access Policies and control access for these vendors using certificates. So, let’s see how we can do that using Microsoft Defender for Cloud Apps and Access Controls. This scenario is covered in the Microsoft official documentation in this link.
Note from the official documentation: Unless the Client app filter is specifically set to Mobile and desktop, the resulting access policy will only apply to browser sessions. The reason for this is to prevent inadvertently proxying user sessions, which may be a byproduct of using this filter. Whilst most major browsers support performing a client certificate check, some mobile and desktop apps use built-in browsers that may not support this check. Therefore, using this filter can affect authentication for these apps.
1 – Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB) that operates on multiple clouds. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your cloud services.
Firstly, let’s import our Root certificate to the Defender for Cloud Apps Portal. To access the portal, go to https://yourtenant.portal.cloudappsecurity.com.
Important: The good news is if you want to test this in a lab like I’m doing, you can use the Microsoft sample certificate. For this, you will need to download the root CA and client certificate provided in the documentation. I am pasting below to facilitate the download, but as a best practice you should visit the official documentation for this.
Now, with the certificate, let’s import the root CA to Defender for Cloud Apps.
In the menu bar select Settings.
Select the Device identification tab.
Upload as many root or intermediate certificates as you require.
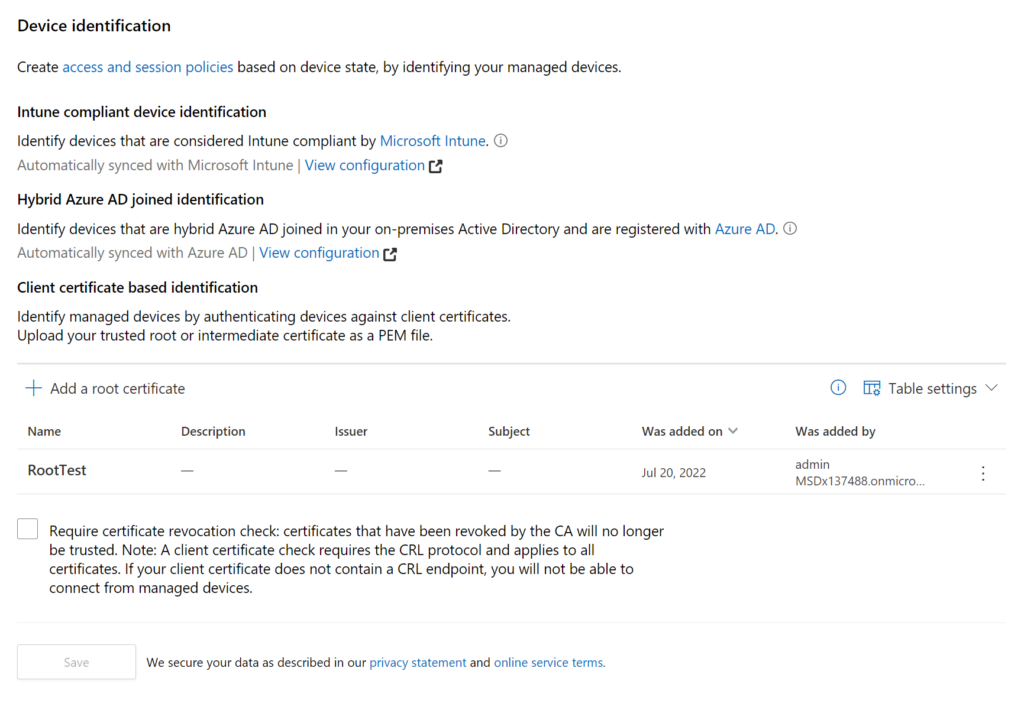
The picture below is from my lab as an example.
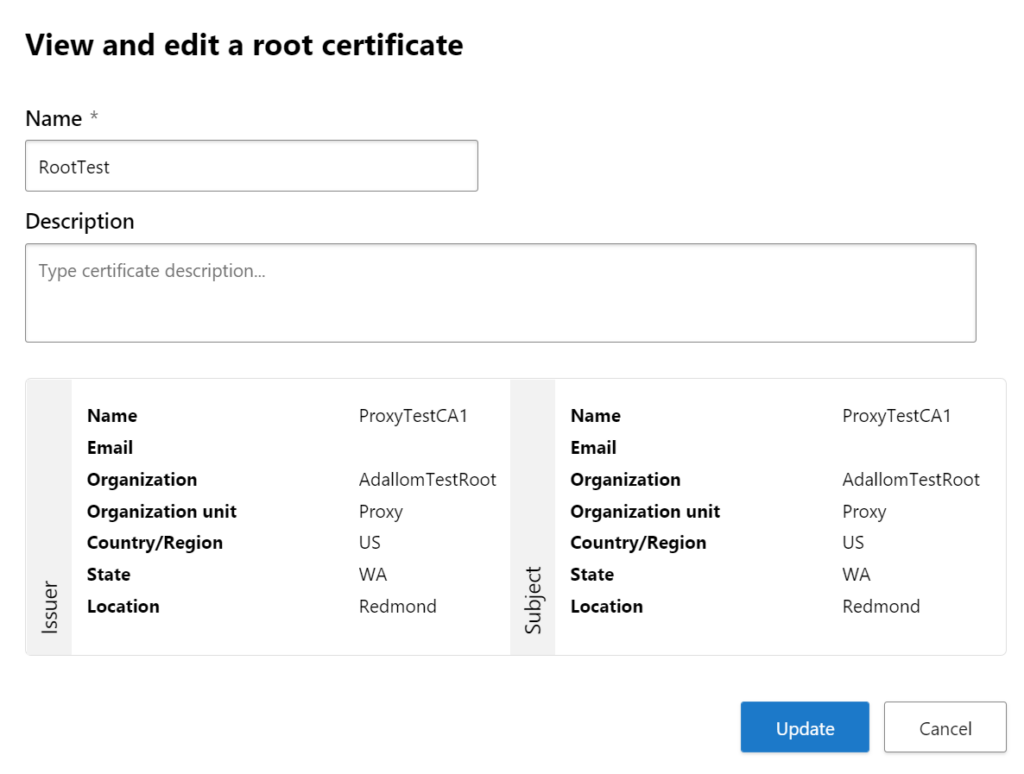
2 – Conditional Access Policy
For this scenario to work, we need to select the application that we want to point to Defender for Cloud Apps to apply a rule on the CASB side. Using Conditional Access Policies, we can instruct Azure AD to validate additional rules on Defender for Cloud Apps, acting as a Reverse Proxy CASB.
For this, let’s access the Azure AD Portal and search for Conditional Access.
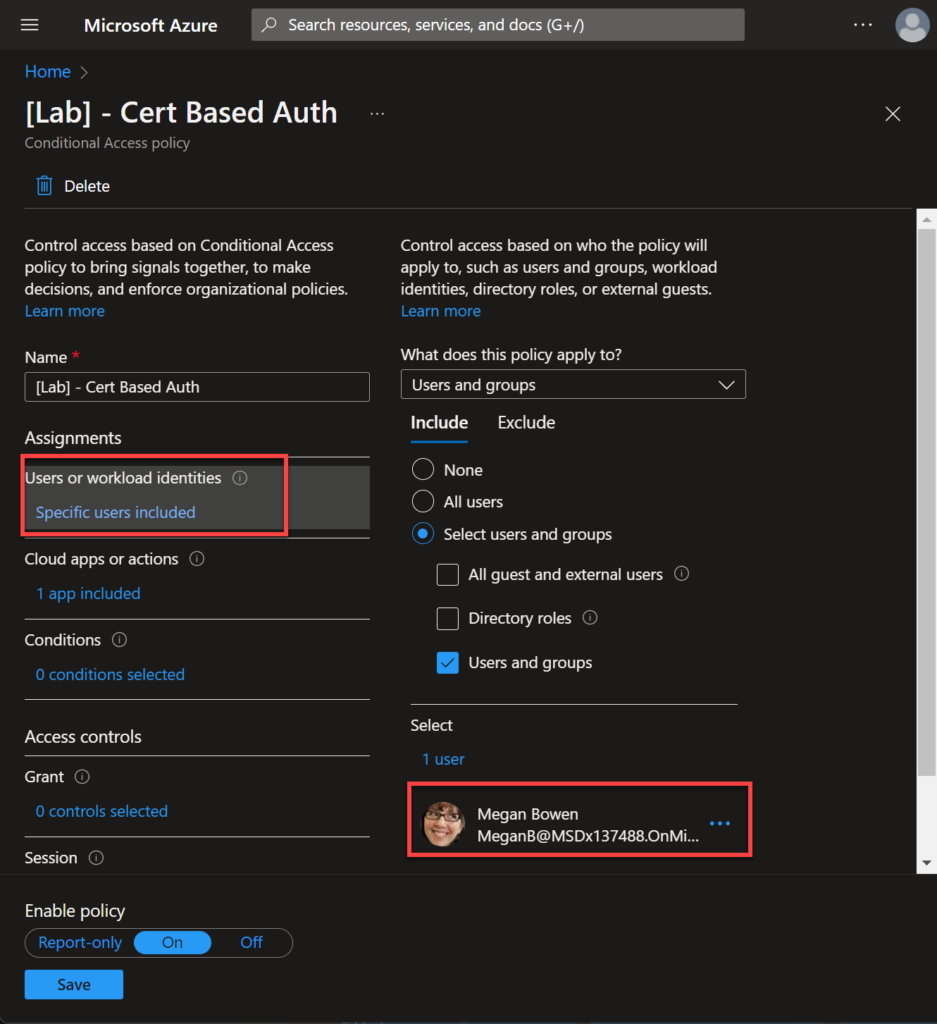
We need to create a new rule and select the users or groups part of the scope.
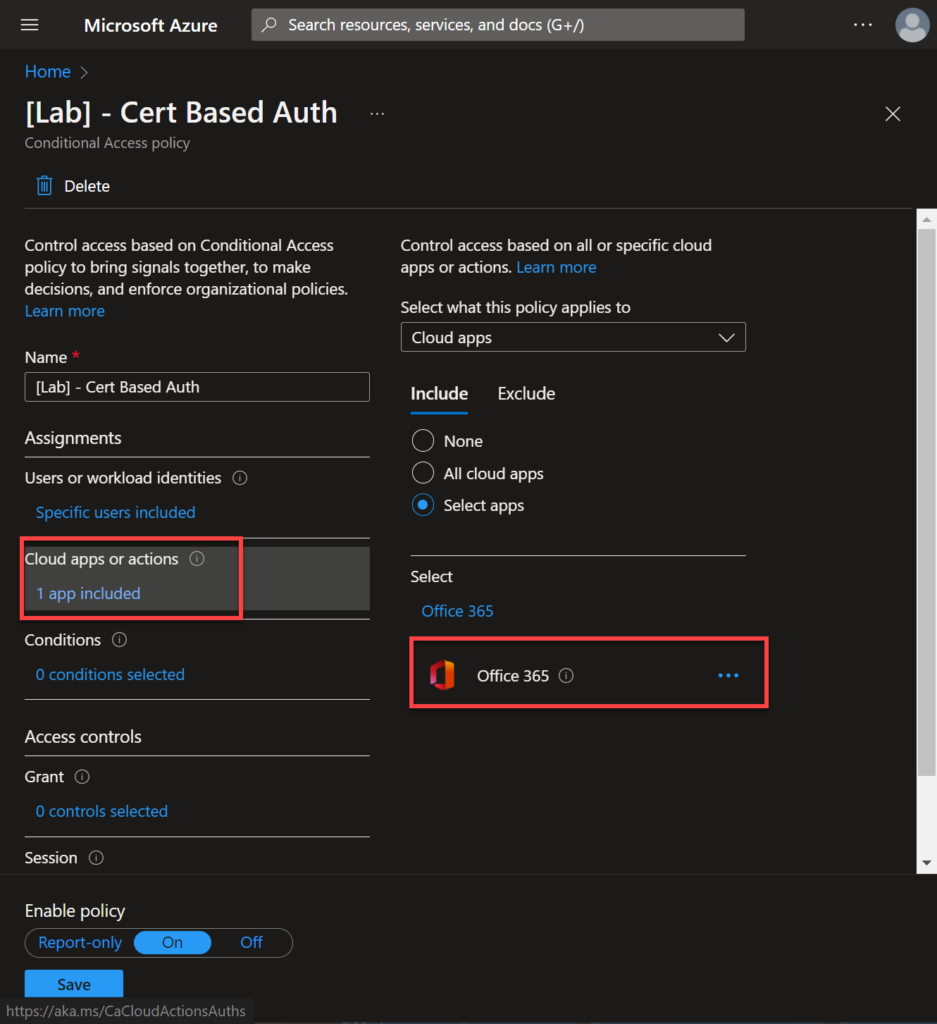
Now, let’s select the application that we want to apply additional rules on the CASB side. In this lab I am using the Office 365 application.
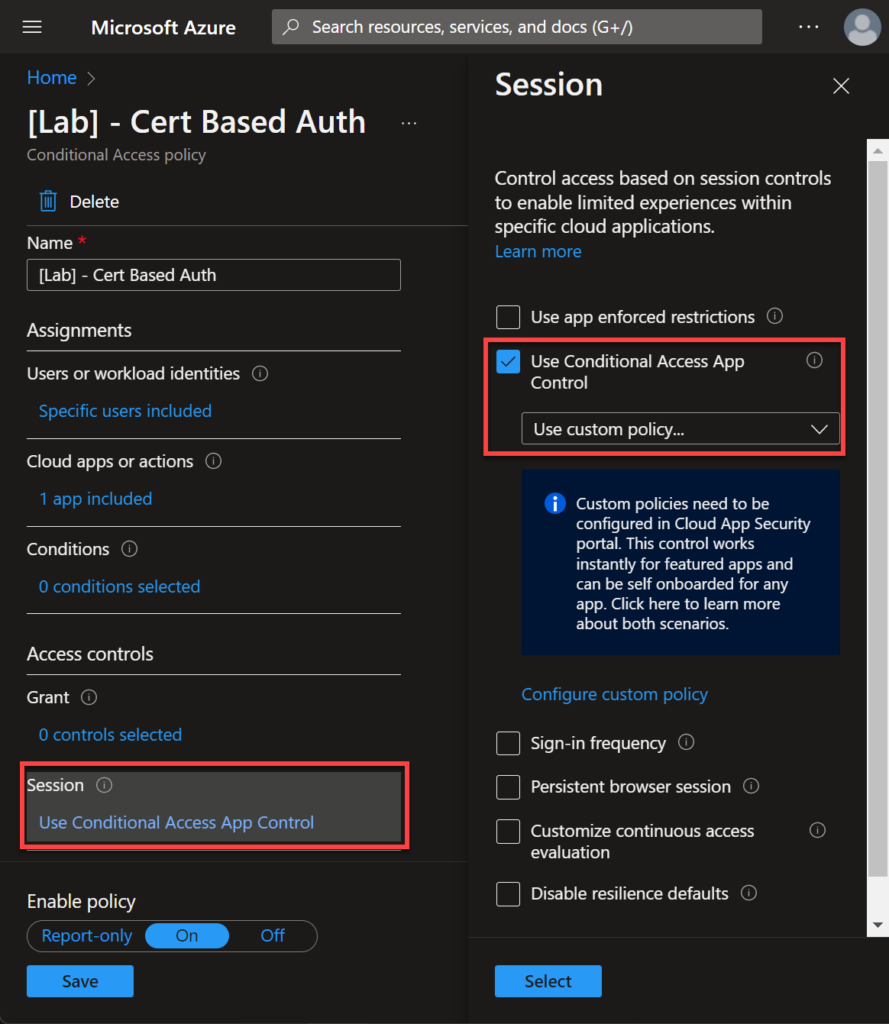
Here is the secret! We need to tell Azure AD to use a Conditional Access App Control like in the image below.
3 – Defender for Cloud Apps policy
So far, our Conditional Access policies validate a specific user/application and redirect to Defender for Cloud Apps to apply additional rules. So, let’s create this rule.
On the Defender for Cloud Apps portal, Navigate to Policies > Conditional Access > Create Policy > Access Policies.
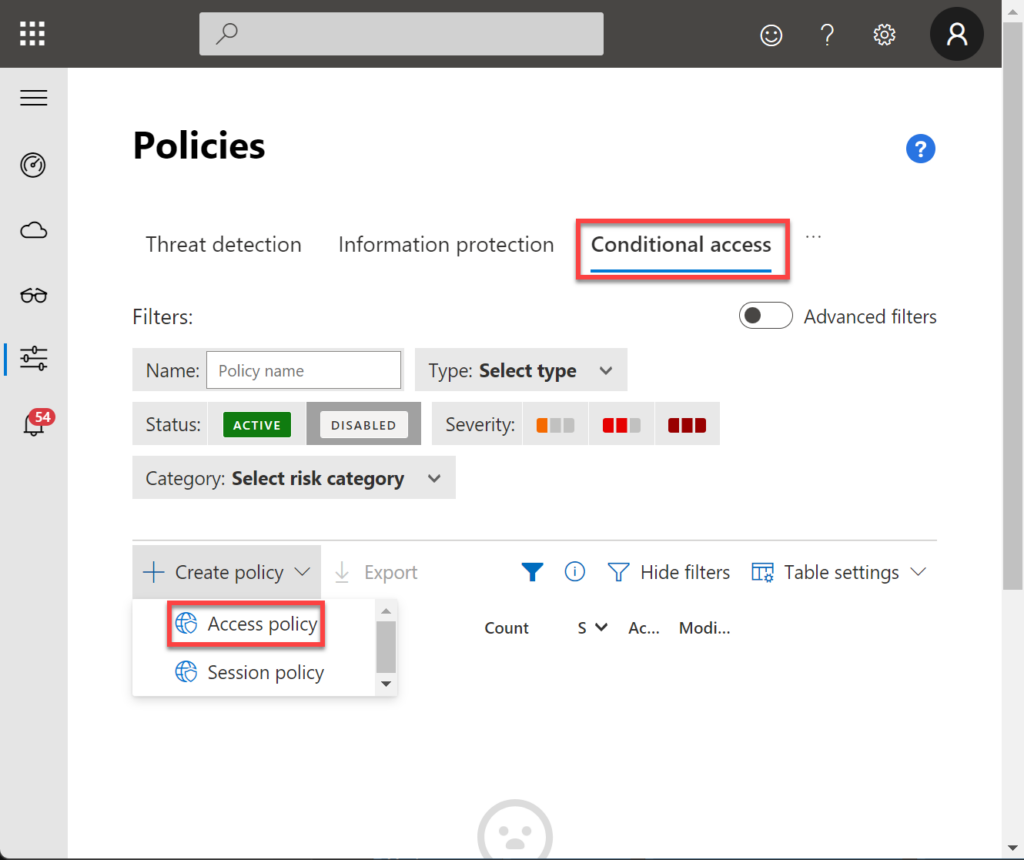
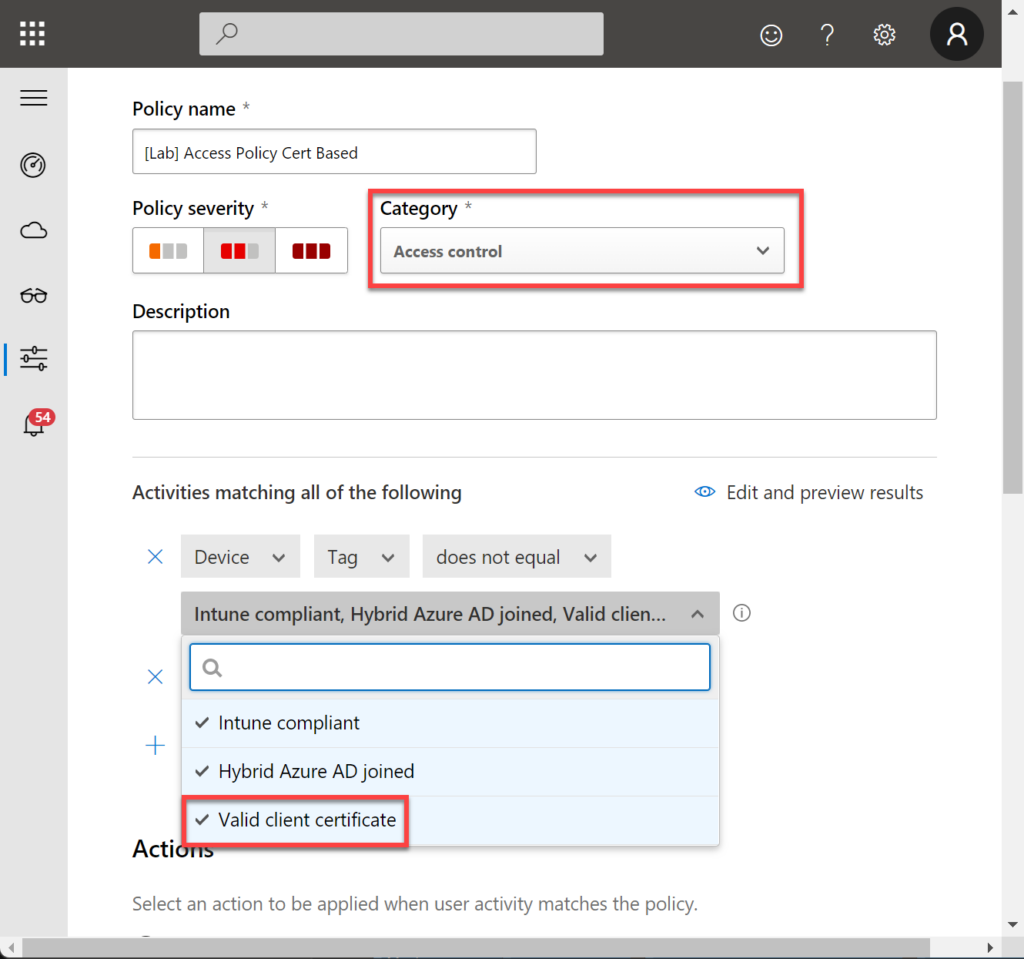
In Category, select Access Control and check if you have Valid client certificate in the filter section.
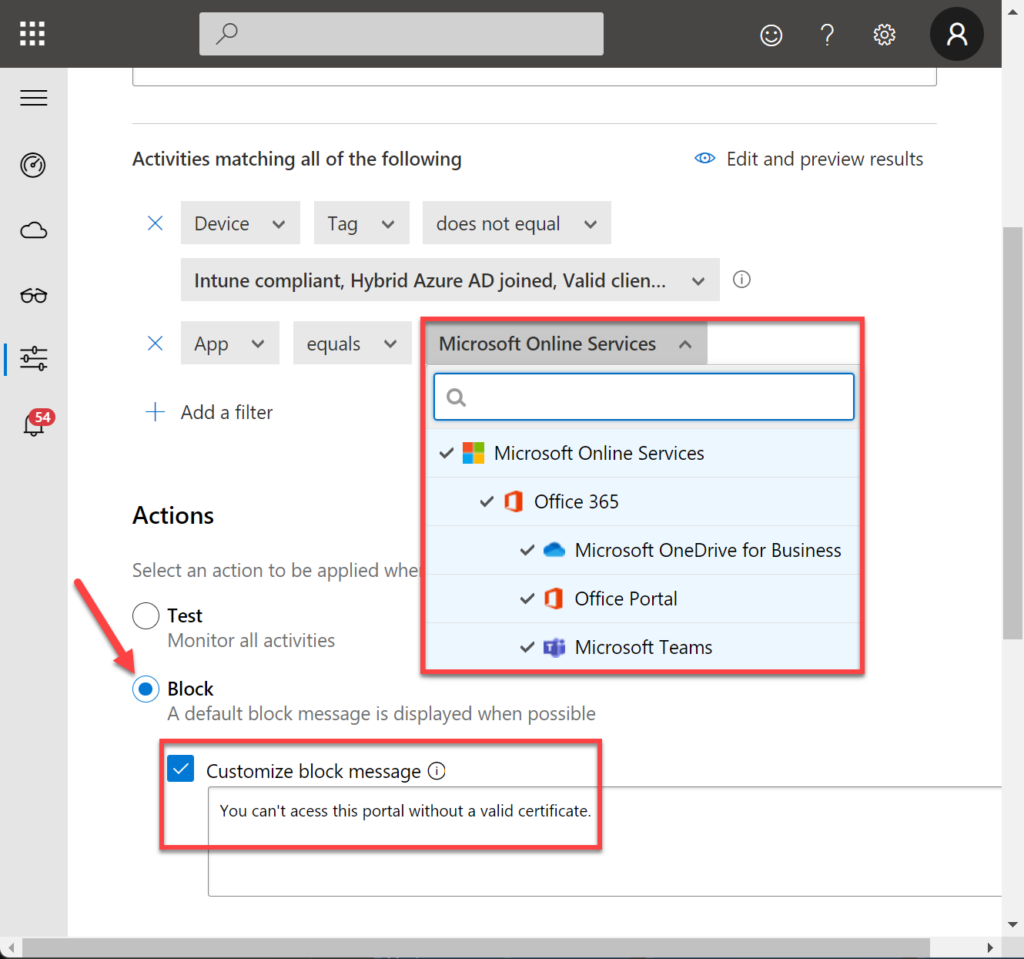
Let’s add the apps we want to apply this rule, in this case: Microsoft Online Services. Also, I will block the access if the user does not have a valid certificate.
4 – Importing the certificates to the client machine
As we have downloaded the Sample Certificates, let’s import the SampleClientCert.pfx to the user we want to test.
Double click on the SampleClientCert.pfx.
Select Current User.
Select the file.
Now, type the password (it’s in the sample files website = Microsoft).
After that, verify that you have the certificate for your Current User.
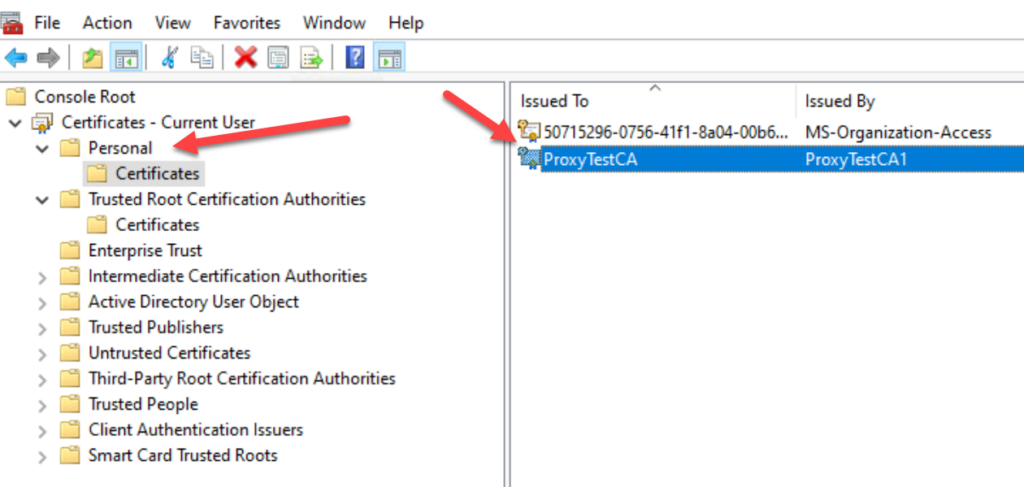
Important: You will need to take the same steps to import the Root CA to the Trusted Root Certification Authorities.
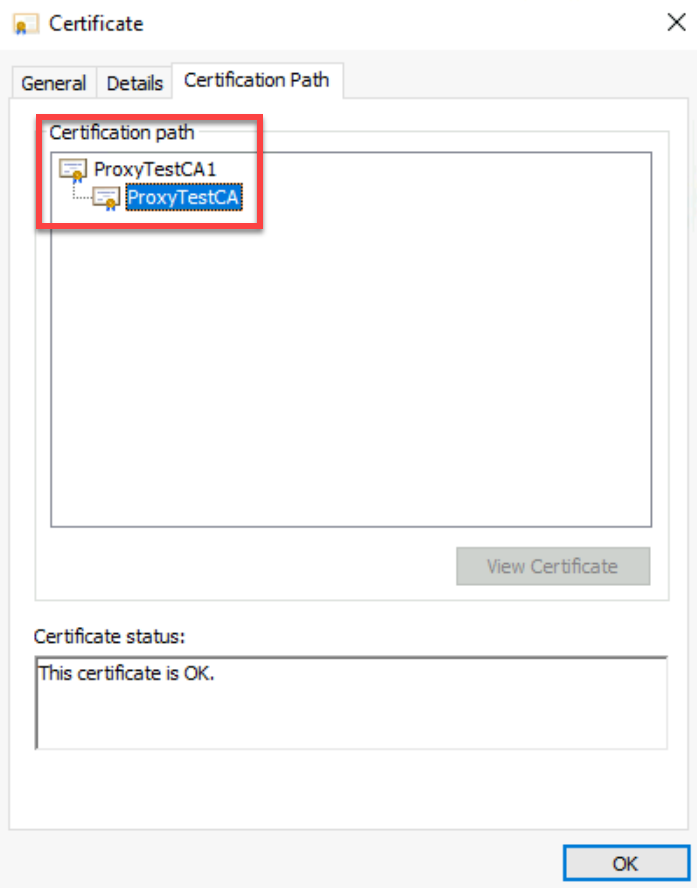
This is needed to validate the certificate path chain.
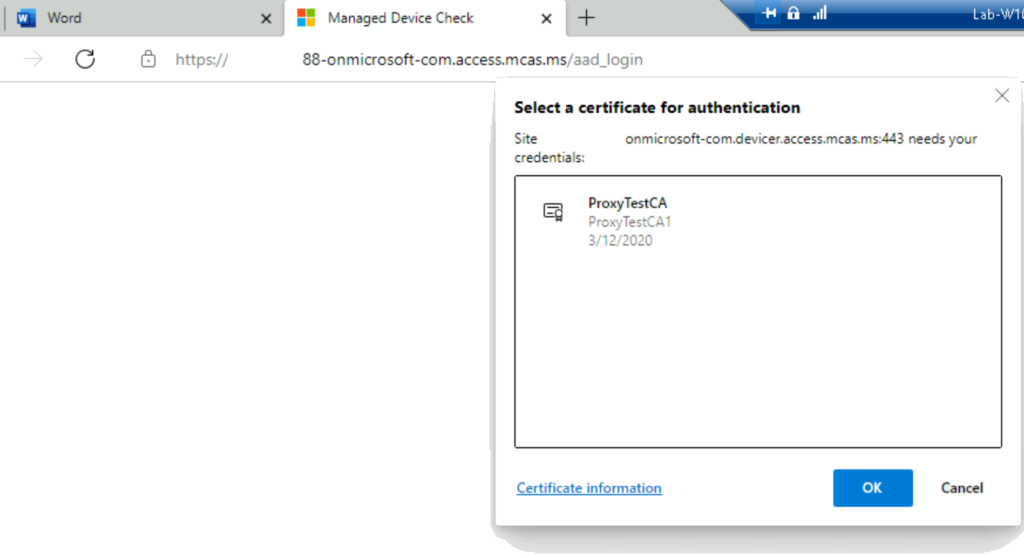
5 – Testing the rule from a client machine
Let’s open the Office portal using a client machine that has the test certificate: https://portal.office.com.
You should get a message like the one below and select the certificate we have imported.
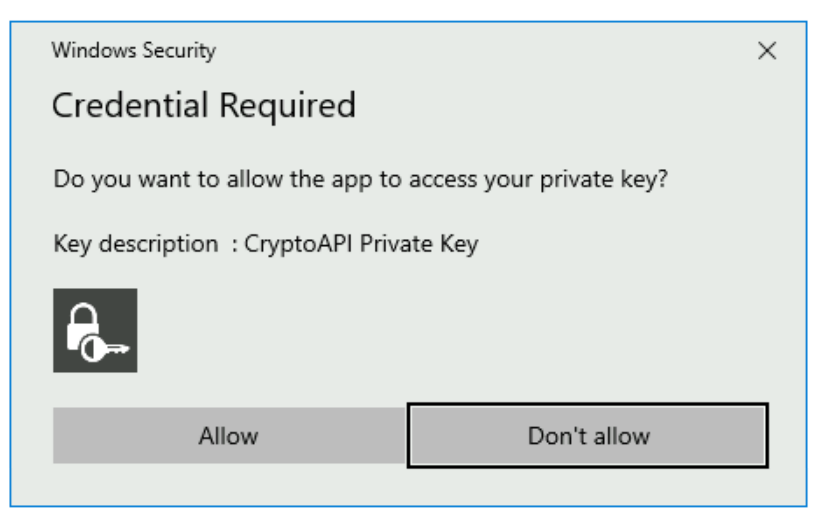
You also need to Allow the app to access the private key.
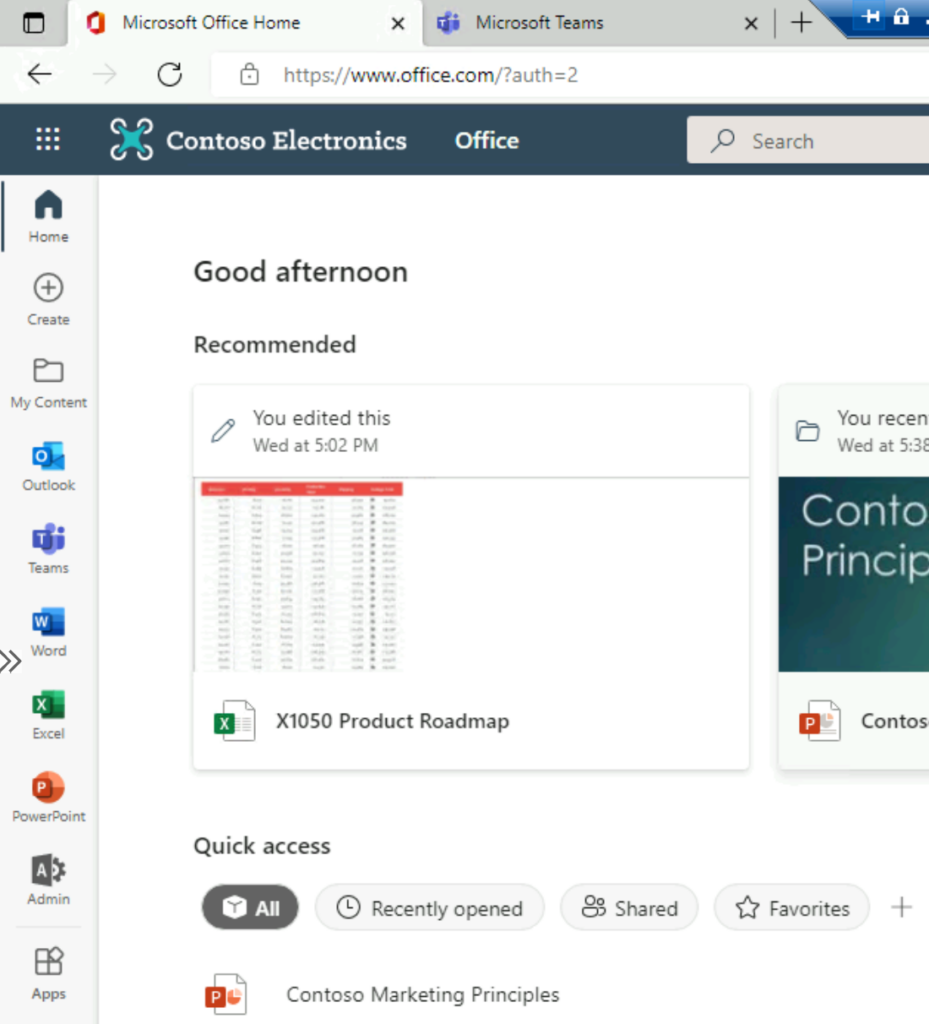
You can now access the portal:
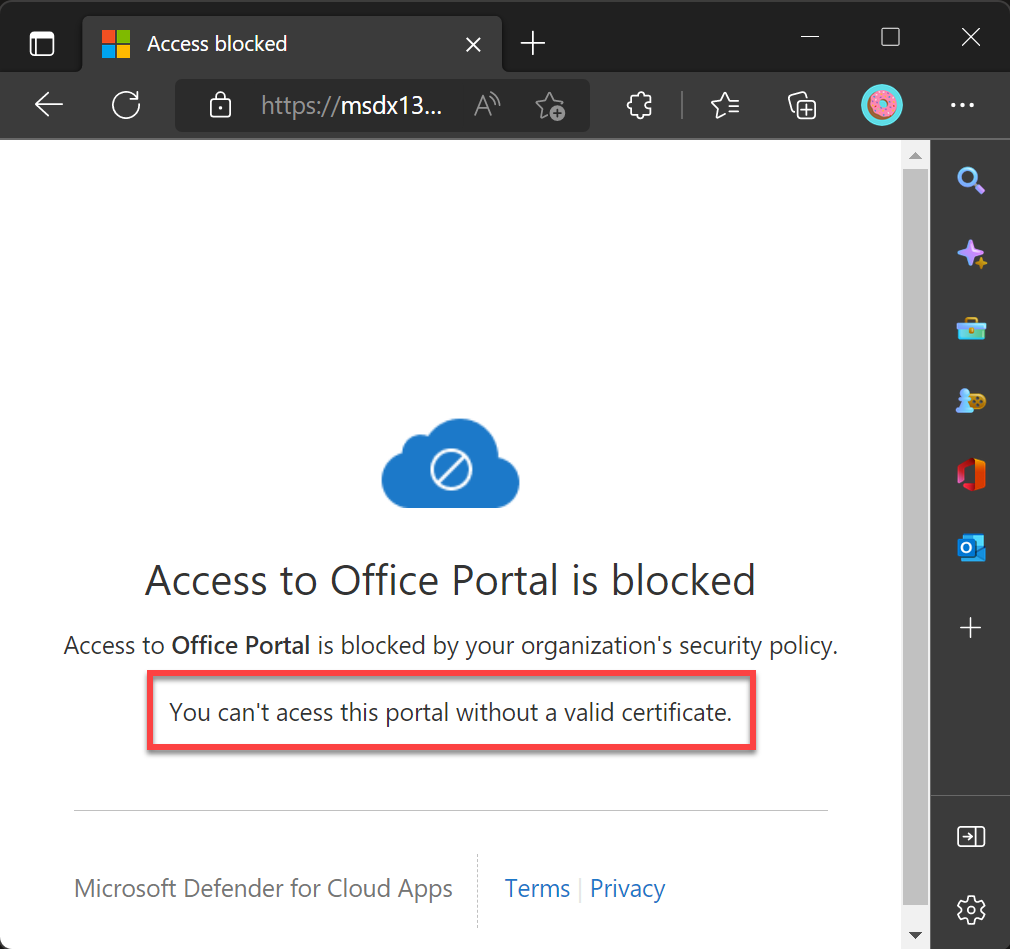
If we try to access the same portal using another machine that does not have the valid certificate, we will get the following message that we customized in our Defender for Cloud Apps.
Summary
In this post, I demonstrated how you could create a session policy to control the access to your cloud apps in Azure using and using a client-certificate rule in your Defender for Cloud Apps to allow a connection only from a client that has a valid certificate.

