Microsoft Sentinel Threat Intelligence – Part III – Using your TI data with Analytics Rules

In my last post, I showed you how to view and manage your threat indicators on the Sentinel portal. Today, I am going to show you what to do with these threat indicators, starting with the analytics rules.
What are Analytics Rules?
One of the most important use cases for threat indicators in a SIEM solution like Microsoft Sentinel is to power threat detection analytics rules. You can configure analytics rules to help you search for specific security events in your environment, correlate a set of events, and configure alerts when you reach certain thresholds or conditions. For example, you can create analytics rules that run on a scheduled basis to generate security alerts for your SOC team to investigate and respond to threats.
When you open the Microsoft Sentinel portal, you have the Analytics blade in the Configuration section.
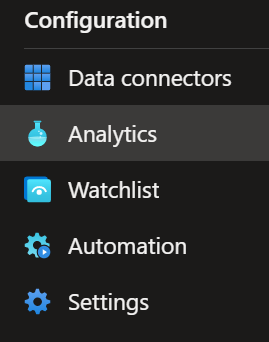
How to use the rules?
You can use either out-of-the-box or customized rules that you can create from scratch using the data you want and correlate signals, for example, matching Threat Intelligence data with information you are getting from your Azure AD sign-in logs.
We can search the out-of-box TI templates on the Analytics blade, Rules templates and look for TI map, as you can see below.
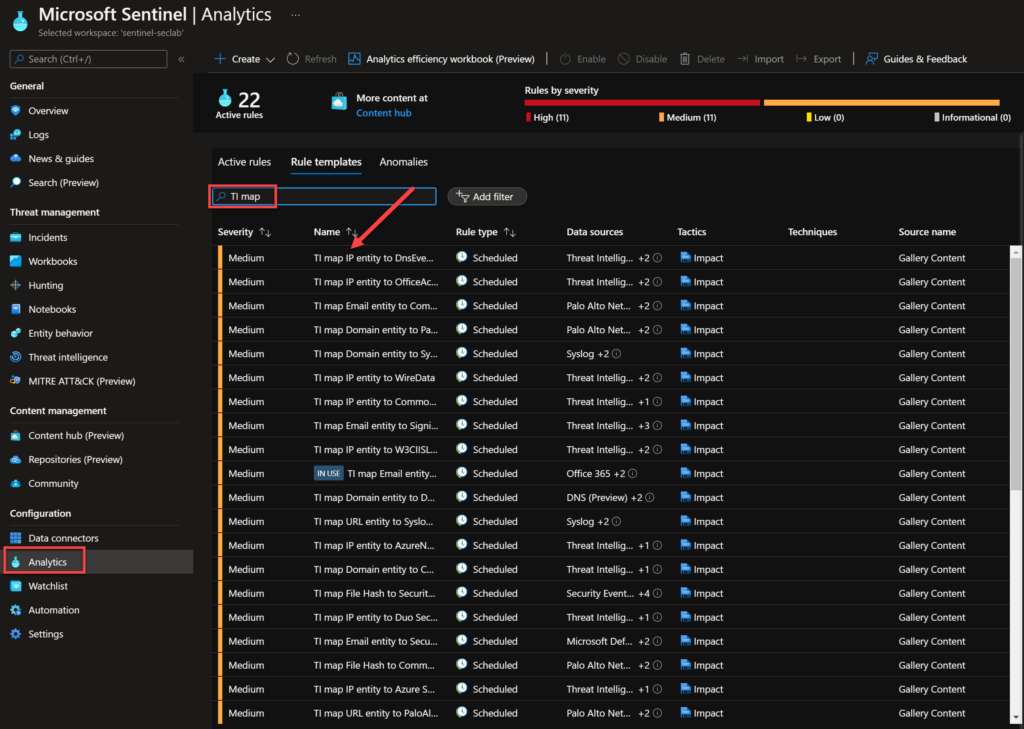
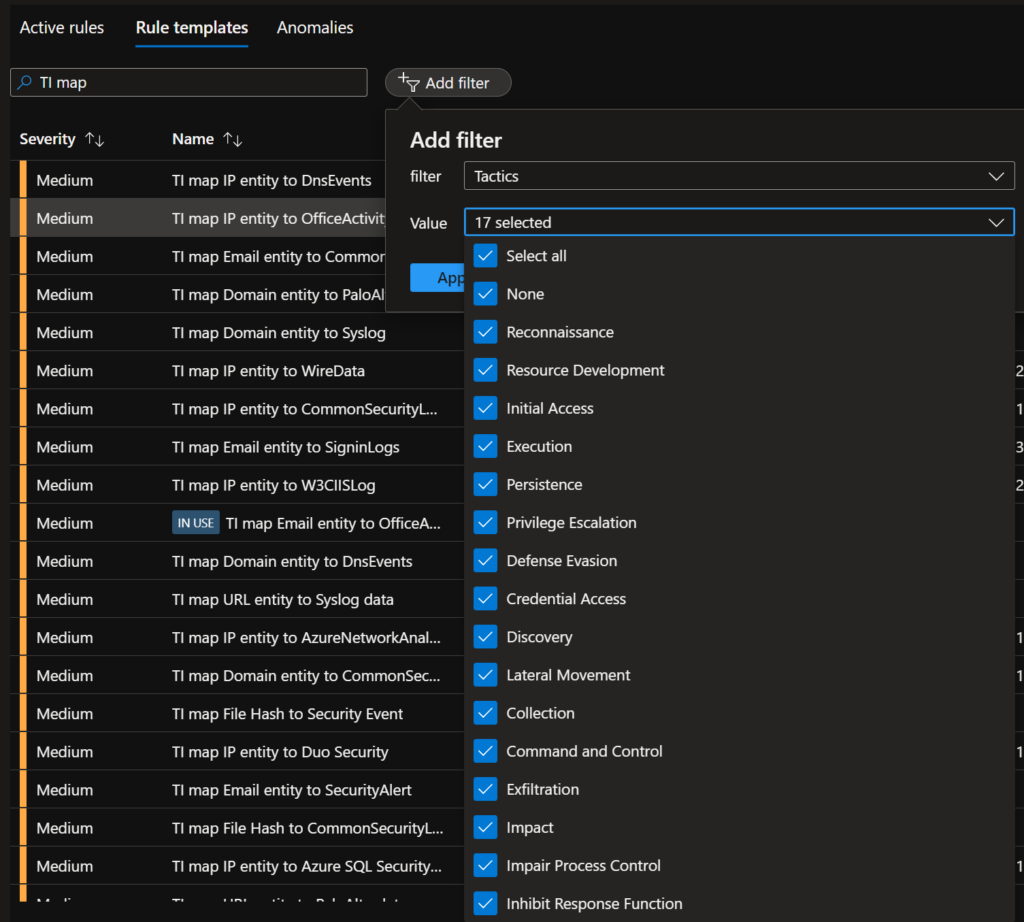
You can also filter the rules templates. In the example below, you can see that I can filter by MITRE Tactics.
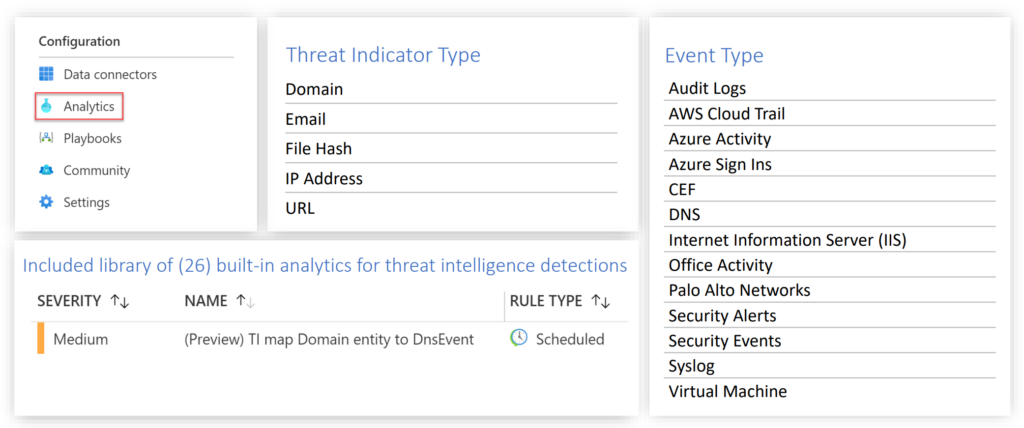
All these rule templates are similar and will give you practical use cases, the difference is the type of threat indicators being used, such as domain, email, file hash, IP address, or URL) and the event type to match.
Basically, the rules will match your threat intelligence data with different types of log data. For example, you can match domain, IP, or URL data from your TI with Azure Activity logs, Office activity data or other event types.
You can see in the example below that you can match the domain indicators that you imported to Sentinel from your TI source with your DNS logs. I got the image below from this informative video on the Microsoft Security Community Channel.
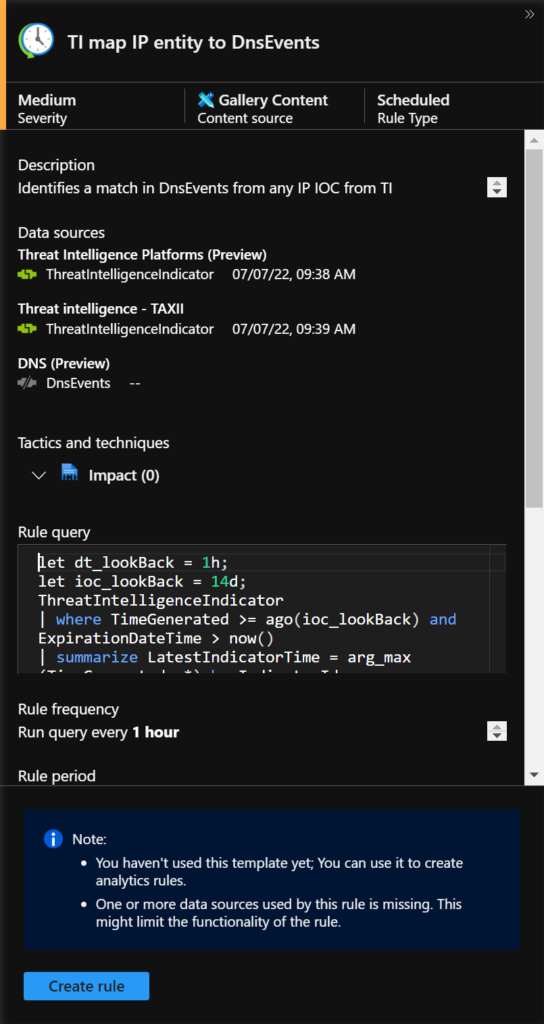
You can see the details on the right blade by selecting a TI map rule from the template.
Creating a rule
To create, go to the Sentinel Portal > Configuration > Analytics > Rule templates > search for TI map > Create rule. In my lab, I am using the TI map IP entity to OfficeActivity.
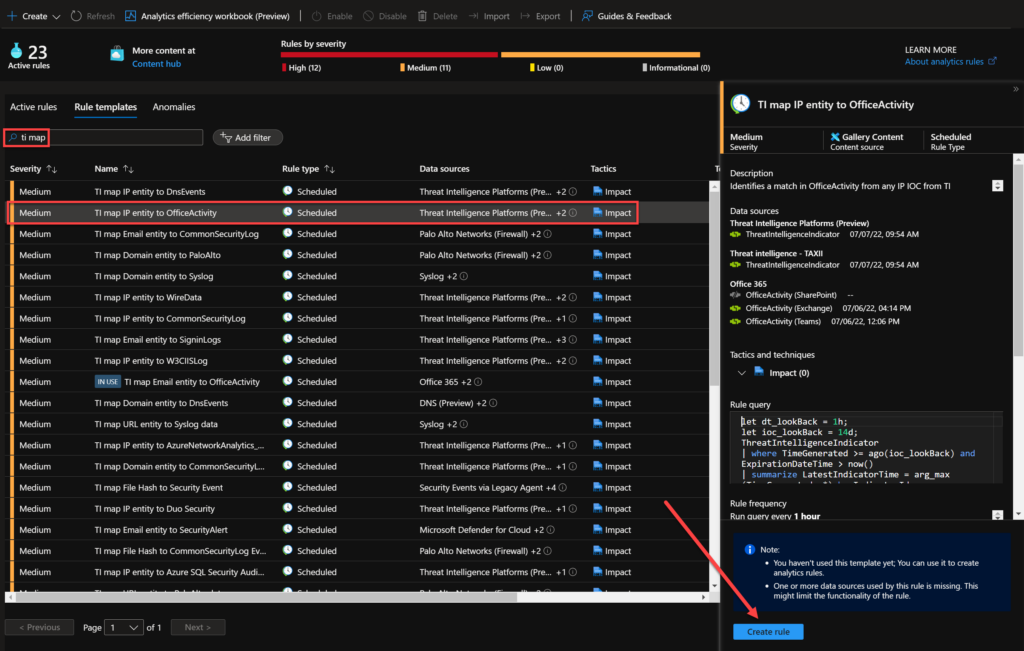
Here, you can change some details like Name, Description, MITRE Tactics and techniques, Severity and Status. After that, click to move to the next page – Set rule logic.
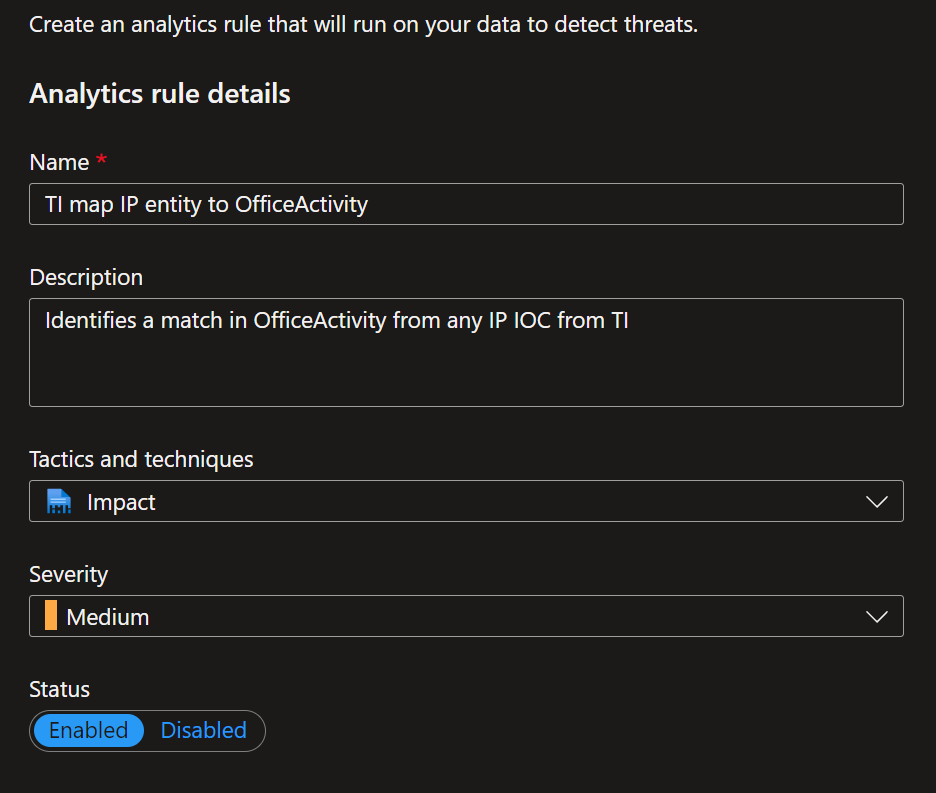
You can define the logic for your analytics rule and modify the KQL (Kusto Query Language) to meet your criteria. Then you can select view query results to analyze your query logic.
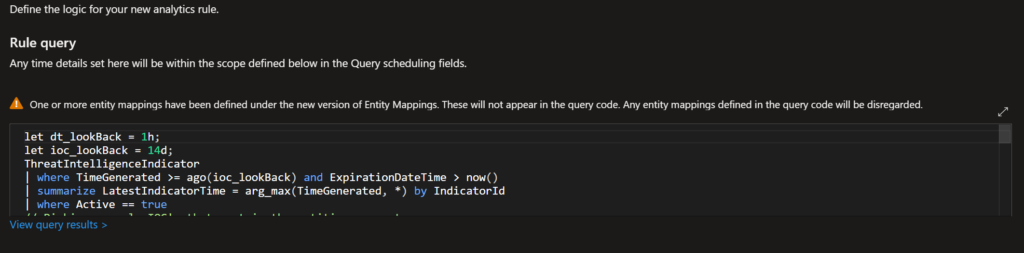
You can configure the alert enrichment with essential information to help you in your investigative processes. You can select entities and identifiers (which are attributes of the entity that help identify the entity as unique).
You can also configure other valuable information such as query scheduling, alert threshold, event grouping, and suppression. I will leave the default for lab purposes.
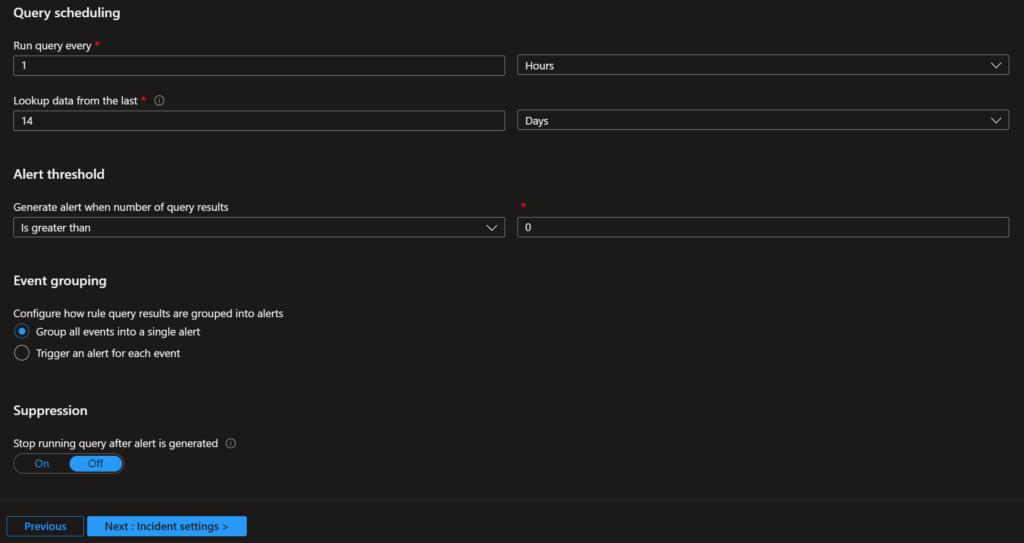
In the incident settings, you can decide if you want to create incidents from alerts triggered by this rule and if you want to group alerts into incidents.
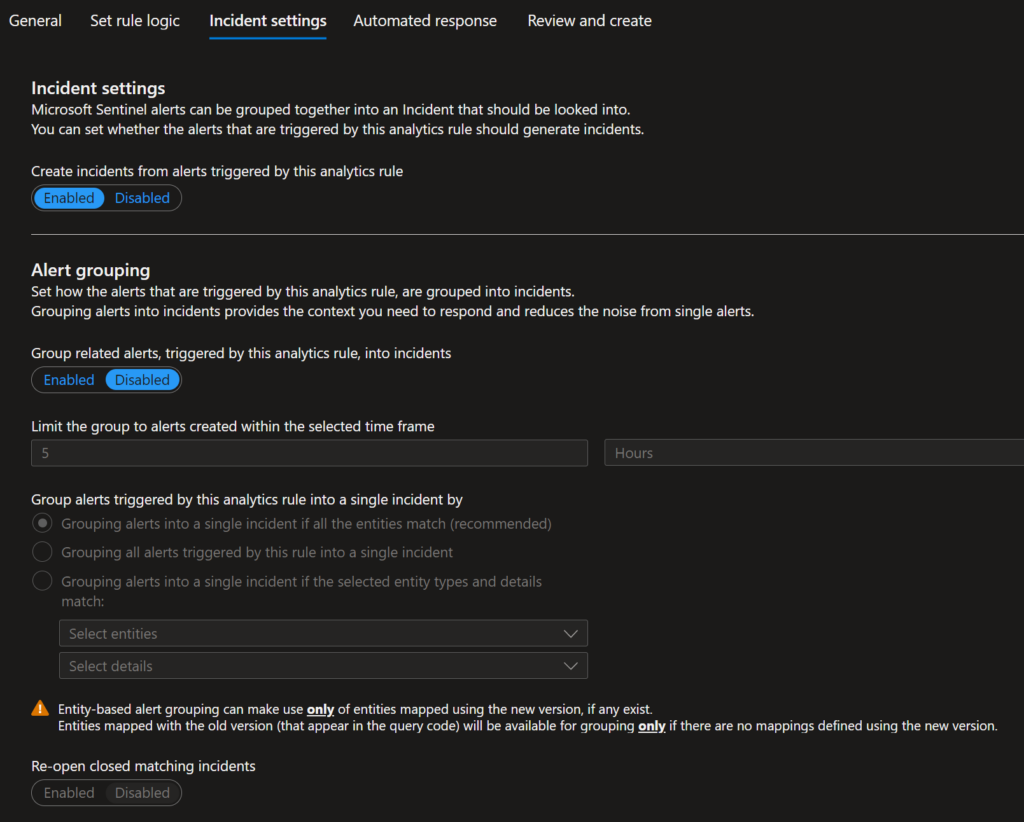
If you have Automation Rules, you can select which one will be triggered by this rule. You will see that you still have the Alert automation (classic); however, Microsoft recommends migrating your alert-triggered playbooks from analytics rules to automation rules.
In the end, you just need to validate and create your rule.
After that, you will see your new rule under Active rules.
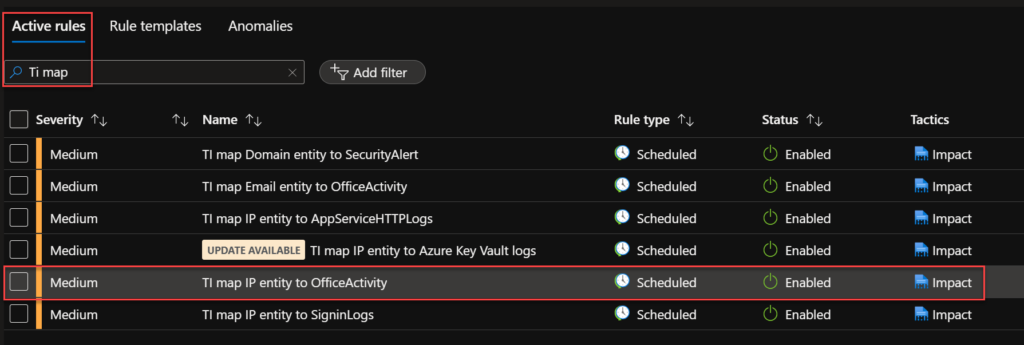
Now, you have your new rule matching IP entity from your threat intelligence feed with your Office activity data connector. You can create your use cases and apply automation to remediate an incident based on the rule logic.
Update 9/23/2022:
In the Microsoft blog post “Microsoft Threat Intelligence Matching Analytics” dated July 27, 2021, and “Microsoft Threat Intelligence Matching Analytics: IP Detections” dated June 16, 2022, Microsoft stated that this matching analytics matches IP and domain indicators from Microsoft with CEF, DNS and Syslog events. On August 2, 2022, Microsoft announced the addition of data from Microsoft Defender Threat Intelligence (MDTI) to this analytic. MDTI is a dedicated threat intelligence portal available from August 2, 2022, based on the internet-mapping capabilities from our acquisition of RiskIQ a little over a year ago.
Mind map to recap (click to enlarge):
I will leave you with a great resource from our Security Community explaining how to explore the Power of Threat Intelligence Recording in Microsoft Sentinel:
References:
Detect threats with built-in analytics rules in Microsoft Sentinel | Microsoft Docs
Detect threats with threat indicator-based analytics
Exercise 3: Analytics Rules based on Threat Intelligence data
Summary
In this post I showed you how to make use of your data coming from your threat intelligence platform using Sentinel analytics rules.