Microsoft Defender for Servers – An Overview – Part I

Microsoft Defender for Servers – Part I
Today, I’d like to present the Defender for Servers plan offered by Microsoft. This plan provides comprehensive protection for your Windows and Linux servers, whether they are running on Azure, AWS, GCP, or on-premises. Furthermore, it seamlessly integrates with Defender for Endpoint, providing a comprehensive, end-to-end threat protection solution.
In the past, we only had the option to license Defender for Servers using a Microsoft Defender for Endpoint standalone license. We’ve migrated defender for servers to a new portal and licensing model within the Defender for Cloud portal. Microsoft Defender for Servers is now a plan that is part of Microsoft Defender for Cloud and must be licensed through it.
Microsoft Defender for Cloud is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) for all your Azure, on-premises, and multi-cloud (Amazon AWS and Google GCP) resources.
Today, to use Defender for Servers, all AWS, GCP, and on-premises machines should be Azure Arc-enabled. Azure Arc helps you onboard Amazon Web Services (AWS), Google Cloud Platform (GCP), and on-premises machines to Azure. Defender for Cloud uses Azure Arc to protect non-Azure machines.
Note: Review the Plan and deploy Azure Arc-enabled servers article to know more. I will cover this topic in a future blog post.
In terms of features, this will give you more flexibility and more security configurations to protect the server altogether. When you enable Microsoft Defender for Servers, you get more features designed to protect your servers, including file integrity monitoring (FIM), adaptive application control, just-in-time access, and more.
Since we’ve migrated to this new model, I’ve been getting a lot of different questions from customers, and I want to explain how to configure Defender for servers using the Defender for cloud Portal. So, I plan to write a series of articles describing how to configure Defender for servers, the best practices, how to manage the log analytics workspaces, permissions, licenses, and when to use Azure Arc.
Note: To get started with Defender for Cloud, you’ll need a Microsoft Azure subscription with Defender for Cloud enabled. If you don’t have an Azure subscription, you can sign up for a free subscription.
Licensing and Pricing
Defender for Servers is offered in two plans.
- Plan 1 provides a limited set of defenses with a focus on Defender for Endpoint and EDR protections.
- Plan 2 (formerly “Defender for servers”) offers the full set of Defender for Cloud’s enhanced security features.
If you open your Defender for Cloud portal using the https://portal.azure.com, go to the Environment Settings and select the Subscription you want, you will see the Defender for Servers plan. When you click on Change Plan, you can see the details.
It is worth noting that Defender for Servers includes licensing for Defender for Endpoint, and also offers cost savings by charging per hour of use instead of per seat. This means that you’ll only pay for the protection of virtual machines when they are active, resulting in lower costs when servers are shut down for maintenance or experience an outage. To put it in perspective, if you were to have servers running 24 hours a day, the maximum cost for the P1 plan would be $5 and the P2 plan would be $15.
You can see the following document to compare both plans:
Select a Defender for Servers plan in Microsoft Defender for Cloud | Microsoft Learn
I really like the visual comparison Tom Janetscheck has published in the Defender blog and I want to share it here with you.
Ref.: Microsoft Defender for Endpoint for Linux and Microsoft Defender for Servers – Microsoft Community Hub
To know more about the pricing model, please visit the Microsoft Defender for Cloud pricing – Pricing—Microsoft Defender | Microsoft Azure. You will be able to check more details about pricing:
Planning
A great place to start learning more about how to plan your deployment is through the following documentation about the deployment plan: Plan a Defender for Servers deployment to protect on-premises and multicloud servers | Microsoft Learn. I got the image below from this website, and this can help you to understand the main stages you have when planning the Defender for Servers deployment.
Workspace Design
You need to understand how Log Analytics workspaces are used in Defender for Servers. When you enable the plan, you can use a default workspace created for the Defender for Cloud in general or set up a custom workspace.
By default, when you enable Defender for Cloud for the first time, a new default workspace will be created in the subscription region (for each subscription).
When you enable the Defender for Servers plan, the plan is enabled for the default workspace, and the Security solution is enabled.
If you have VMs in multiple locations, Defender for Cloud creates multiple workspaces accordingly to ensure data compliance.
Default workspace names are in the format [subscription-id]-[geo].
If you are running Microsoft Sentinel (Microsoft’s SIEM/SOAR) it’s important to note these best practices regarding Workspaces:
Use the same workspace for both Microsoft Sentinel and Microsoft Defender for Cloud, so that all logs collected by Microsoft Defender for Cloud can also be ingested and used by Microsoft Sentinel. The default workspace created by Microsoft Defender for Cloud will not appear as an available workspace for Microsoft Sentinel.
Since Defender for Cloud uses the Log Analytics infrastructure, it is important to verify the Log Analytics agent and Azure Monitor agent options you have. Check the following article to know more – Plan Defender for Servers agents and extensions deployment | Microsoft Learn.
Settings and Monitoring
If you head over to your Defender for Cloud portal and select Environment Settings and Defender Plans, you will see the Settings & Monitoring option.
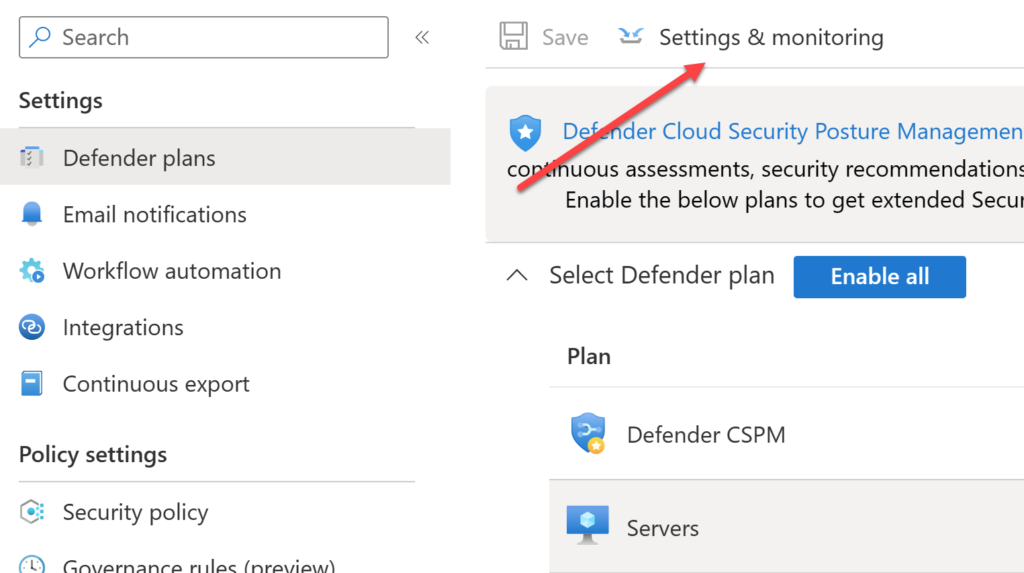
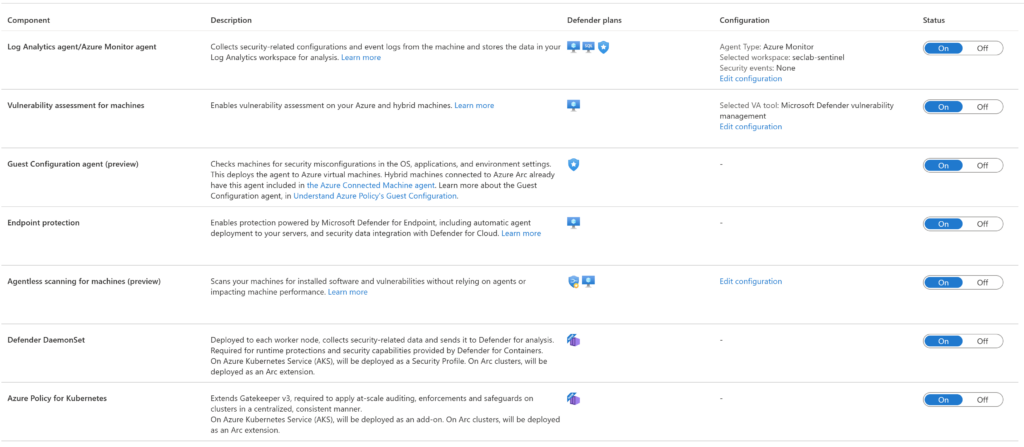
You can use these settings to change some of the components, like the log analytics/azure monitor agent.
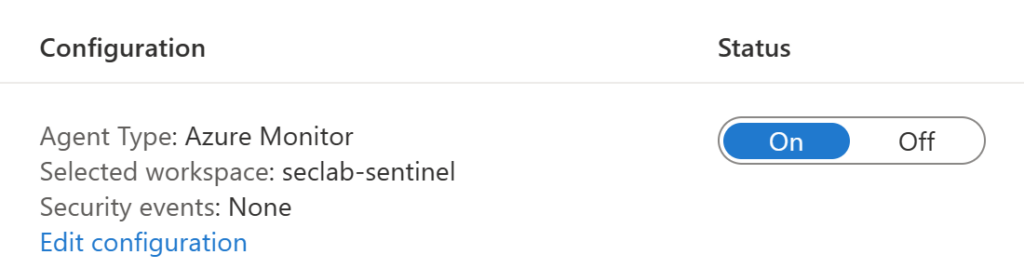
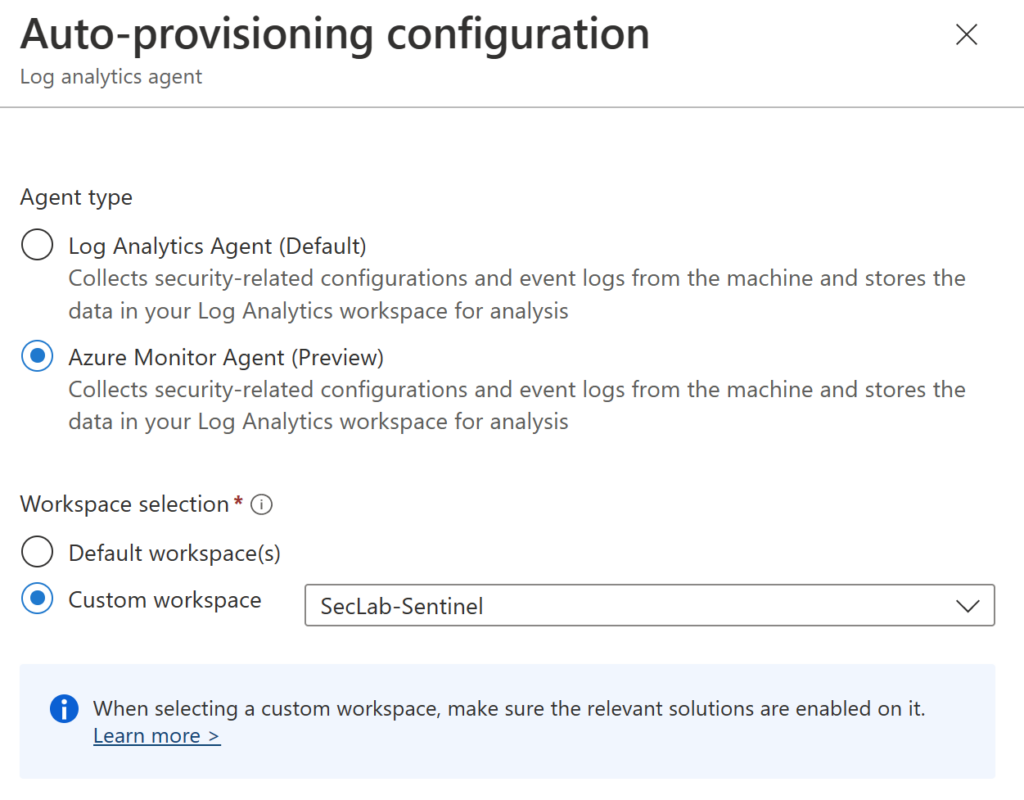
Here, you can change your workspace. For example, in my lab, I am pointing it to the Microsoft Sentinel Workspace. Click on Edit Configuration to see the options available.
Another example (and I’ll cover this topic in a future article) is to change the default vulnerability assessment solution:
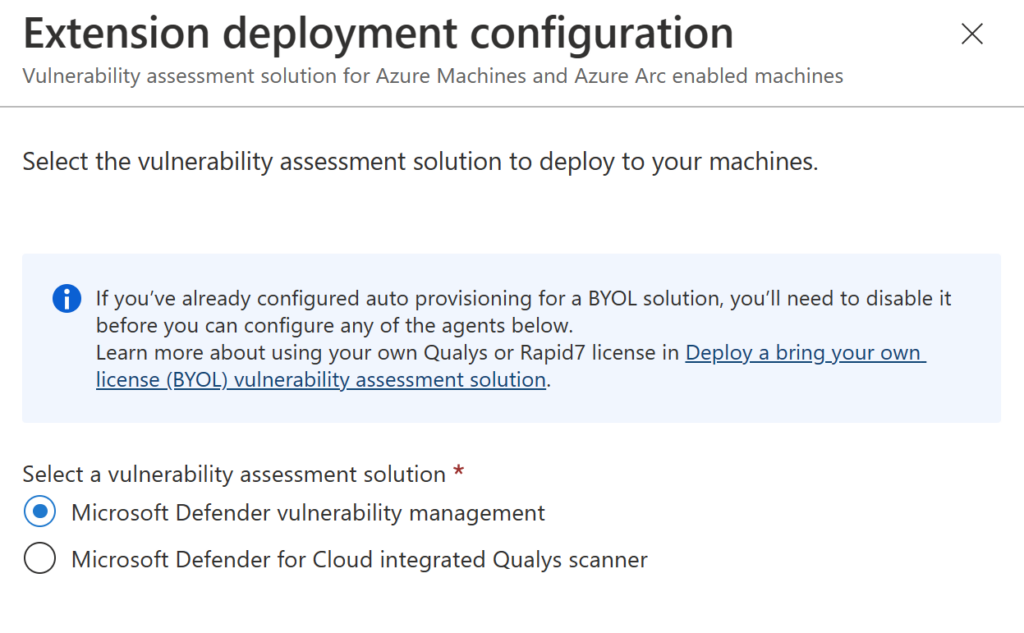
On the same page, you can change settings such as the endpoint protection integration, configure the agentless scanning for VMs, set the guest configuration agent, and more.
Permissions and Roles
Defender for Cloud basically has two built-in roles to control Defender for Cloud access:
- Security Reader: Provides viewing rights to Defender for Cloud recommendations, alerts, security policy, and states. This role can’t make changes to Defender for Cloud settings.
- Security Admin: Provides Security Reader rights and the ability to update security policy, dismiss alerts and recommendations, and apply recommendations.
Ref.: Plan Defender for Servers roles and permissions | Microsoft Learn
Enabling the Plan
Enabling Defender for Servers is quite easy after you plan it. You just need to head over to your Defender for Cloud portal, Environment Settings, Select the subscription, and turn on the plan like the image below.
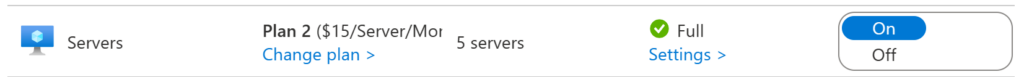
To choose between P1 or P2 plan click on the Change plan option and select the one you want to deploy.
Defender for Endpoint Integration and Extensions
Defender for Endpoint Integration
As I mentioned earlier, there is a native integration between Defender for Servers and Microsoft Defender for Endpoint, which is the service that is going to provide endpoint detection and response (EDR) and other threat protection features. These are the same features that are provided by Microsoft Defender for Endpoint Plan 2, however, when it comes to the server license, you are going to get the same MDE P2 protections as part of the Server P1 plan as you can see in the image below:
You can check the list of features below:
– Attack surface reduction to lower the risk of attack.
– Next-generation protection, including real-time scanning and protection and Microsoft Defender Antivirus.
– EDR, including threat analytics, automated investigation and response, advanced hunting, and Microsoft Defender Experts.
– Vulnerability assessment and mitigation provided by Defender for Endpoint integration with Microsoft Defender Vulnerability Management.
After enabling the Defender for Servers plan, you will get the Defender for Endpoint extension that will be automatically deployed to your servers and used to deploy and integrate the Defender for Endpoint sensor on the machine.
Regarding the OS support for MDE for Windows, you can install it on the following versions:
- Windows Server 2008 R2
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server Semi-Annual Enterprise Channel
- Windows Server 2019 and later
- Windows Server 2019 core edition
- Windows Server 2022
For Linux requirements, please check Microsoft Defender for Endpoint on Linux | Microsoft Learn.
If you are running VMs on Azure, you can check the agent extension by opening your VM properties and selecting Extensions + applications.
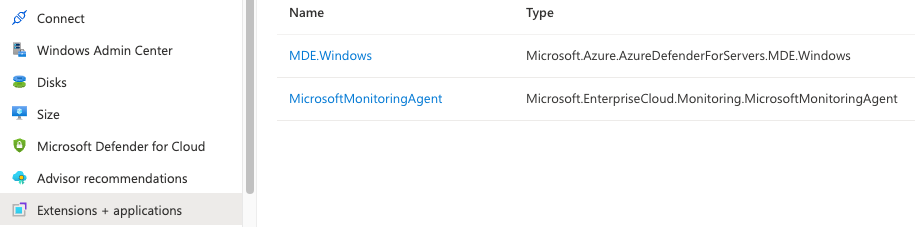
- Windows machines extension:
MDE.Windows - Linux machines extension:
MDE.Linux - Machines must meet minimum requirements.
- Some Windows Server versions have specific requirements.
Ref.: Plan Defender for Servers agents and extensions deployment | Microsoft Learn
Please, check other provisioning considerations on this link: Plan Defender for Servers agents and extensions deployment | Microsoft Learn
Protection features part of the P2 plan
In addition to the Server P1 features, I want to cover here the P2 features that will give you an extra layer of protection for your servers, such as:
Threat detection for network-level (agentless)
Defender for Servers detects threats that are directed at the control plane on the network, including network-based detections for Azure virtual machines.
Microsoft Defender Vulnerability Management Add-on
See a deeper analysis of the security posture of your protected servers, including risks related to browser extensions, network shares, and digital certificates.
Qualys vulnerability assessment
As an alternative to Defender Vulnerability Management, Defender for Cloud integrates with the Qualys scanner to identify vulnerabilities. You don’t need a Qualys license or account.
Adaptive application controls
Adaptive application controls define allowlists of known safe applications for machines. To use this feature, Defender for Cloud must be enabled on the subscription.
Free data ingestion (500 MB) in workspaces
Free data ingestion is available for specific data types. Data ingestion is calculated per node, per reported workspace, and per day. It’s available for every workspace that has a Security or AntiMalware solution installed.
Just-in-time virtual machine access
Just-in-time virtual machine access locks down machine ports to reduce the attack surface. To use this feature, Defender for Cloud must be enabled on the subscription.
Adaptive network hardening
Network hardening filters traffic to and from resources by using network security groups (NSGs) to improve your network security posture. Further improve security by hardening the NSG rules based on actual traffic patterns. To use this feature, Defender for Cloud must be enabled on the subscription.
File integrity monitoring
File integrity monitoring examines files and registries for changes that might indicate an attack. A comparison method is used to determine whether suspicious modifications have been made to files.
Docker host hardening
Assesses containers hosted on Linux machines running Docker containers, and then compares them with the Center for Internet Security (CIS) Docker Benchmark.
Network map
Provides a geographical view of recommendations for hardening your network resources.
Agentless scanning
Scans Azure virtual machines by using cloud APIs to collect data.
Tips and Tricks
To wrap up our first article about Defender for Servers I want to leave you with some additional considerations:
- You must enable Defender for Servers P2 at the Subscription and Workspace levels. When you enable the plan on an Azure Subscription or AWS/GCP account, all your servers will be protected by Defender for Servers. There are no methods to apply to a subset of servers.
- Defender for Servers Plan 1 does not depend on Log Analytics. When you enable Defender for Servers Plan 2 at the subscription level, Defender for Cloud automatically enables the plan on your default Log Analytics workspaces. If you use a custom workspace, make sure you enable the plan on the workspace. More details here.
- Defender for Servers does not support endpoint OSs. For this, you will need a Microsoft Defender for Endpoint plan.
PoC and Trial
To learn more about how to run a Defender for Servers PoC, I strongly recommend reading the following article from the product team – Microsoft Defender for Cloud PoC Series – Defender for Servers – Microsoft Community Hub.
Scaling your deployment
To conclude, I want to leave you with an article to help you to scale your deployment – Scale a Defender for Servers deployment | Microsoft Learn.
Common Questions and FAQ – FAQ for Microsoft Defender for Servers | Microsoft Learn
Summary
In this blog post, I showed you all the essential information you need to understand more about the Defender for Servers plan.
In the next Defender for Server article, I will cover more of the advanced features part of the P2 plan, including how to install the Azure Arc agent to connect your on-premises servers and other clouds, such as AWS and GCP.
Thank you!
