Zero Trust Maturity Mind Maps

Zero Trust Maturity Mind Map
Reference: Evolving Zero Trust – Microsoft Position Paper.
Ever since the term Zero Trust came out regarding cyber security, manufacturers, partners, and professionals have provided a range of perspectives. Some manufacturers provide Zero Trust to one specific area like identity or devices. Some businesses may view Zero Trust as something to buy off the shelf.
The reality, however, is that Zero Trust is a process or strategy if you will. It is also a moving target in the since that, with recent technologies and approaches, the ability to achieve Zero Trust is always ongoing.
In this context Microsoft takes the following approach to Zero Trust. First, we look at three major principles.
- Verify Explicitly
- Least Privilege Access
- Assume Breach
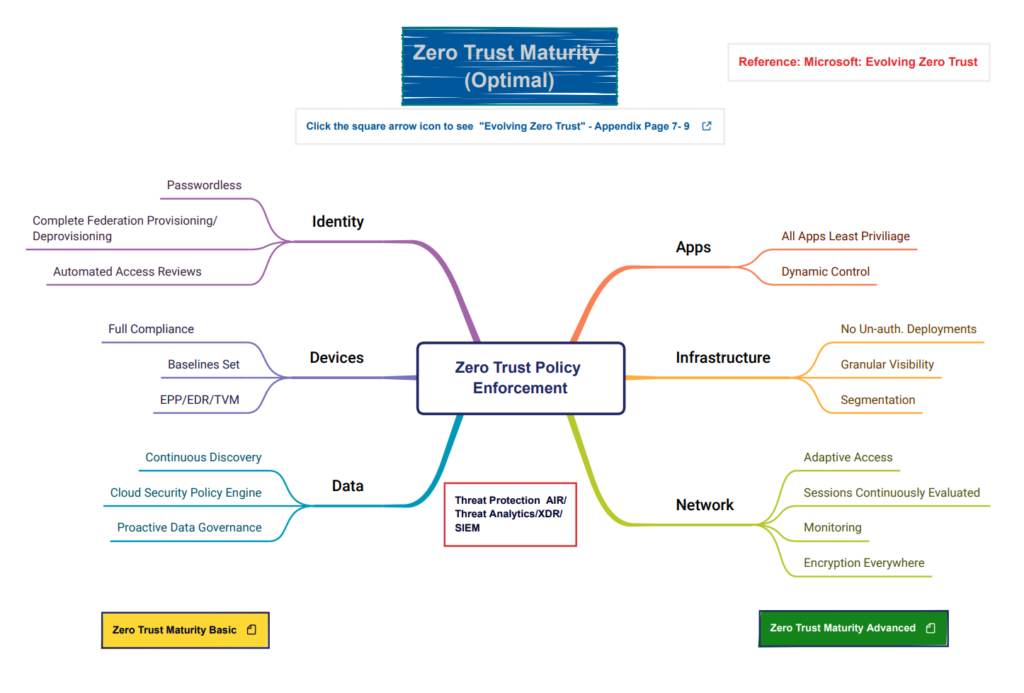
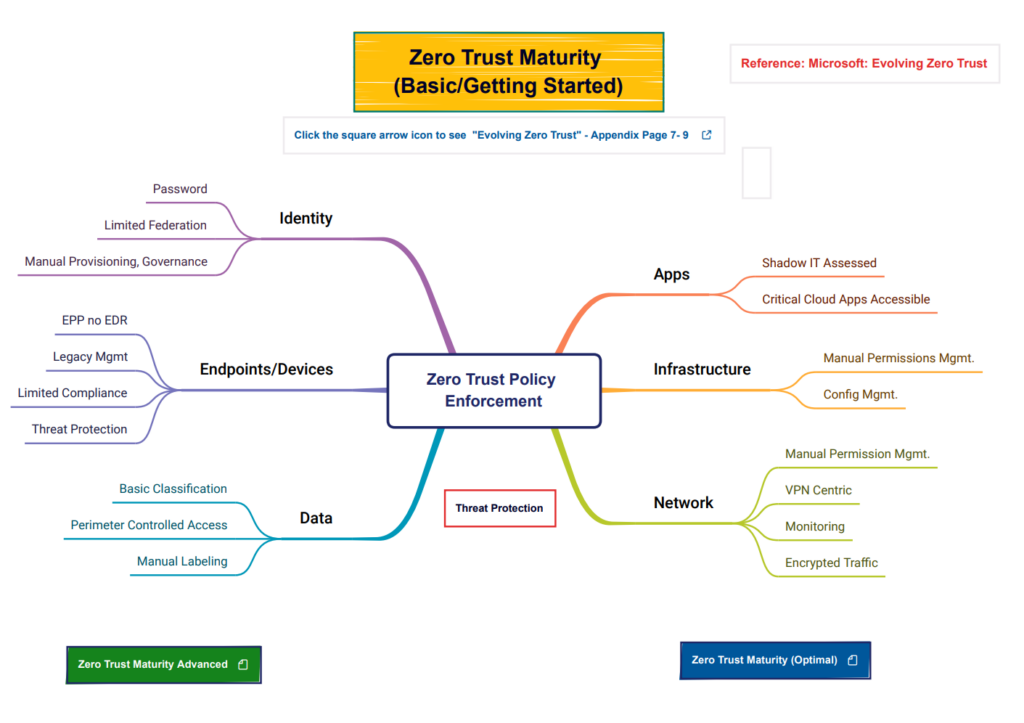
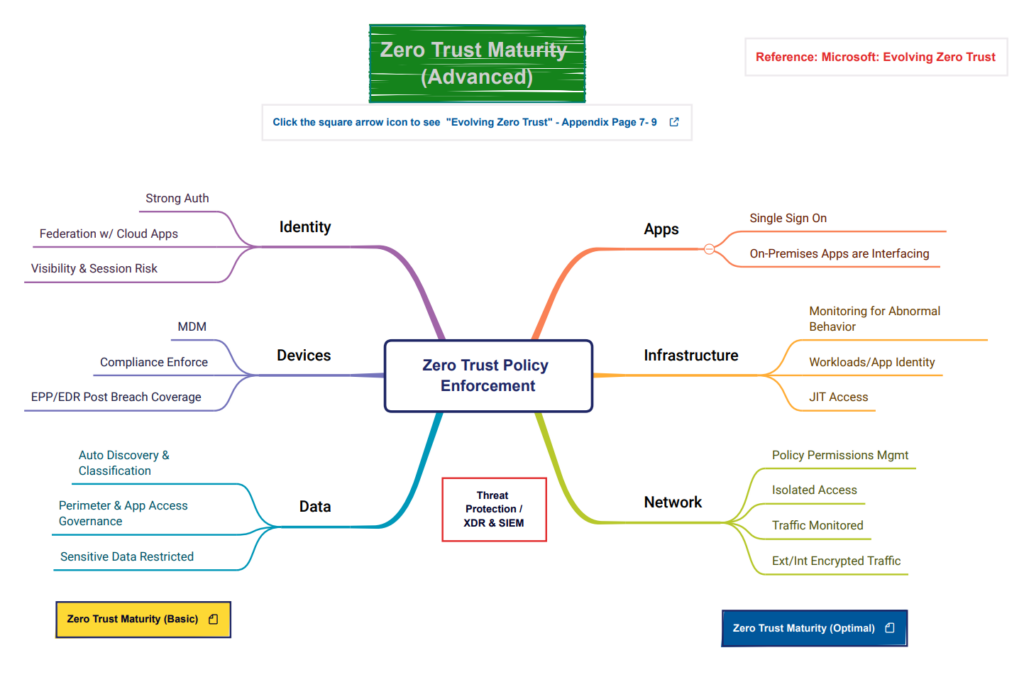
Second, we look at six major pillars where Zero Trust needs to be applied. These pillars are all interconnected and make up an IT ecosystem and are applied to on-premises and multi-cloud environments.
- Identity
- Endpoint/Devices
- Apps
- Data
- Infrastructure
- Network
Lastly, there is a set of Zero Trust Policies that run throughout the six pillars.
- Policy Enforcement
- Threat Protection
Because this is comprehensive and covers an IT ecosystem, Zero Trust needs to be looked at from a maturity level rather than from a point solution or a set of solutions.
The mind map models in this section cover three maturity models, Basic/Getting Started, Advanced, and Optimal. Each model has a link that explains the six pillars and how they relate to a maturity level for each model.
Because we look at this from a maturity standpoint, the question is not if businesses are doing Zero Trust, most are doing some portion, but how mature are they in the Zero Trust process and at what level within each pillar.
By taking this approach, security professionals can look at the environment and determine the gaps and how to address them.
We hope these models help to clarify what it means to have Zero Trust within a business and empower security teams to build a solid Zero Trust foundation.
Jeff Van Gundy TS-Security, Microsoft
Jeff Van Gundy, CISSP | LinkedIn
“Most businesses aren’t in the business of security, but security can help them stay in business.”
All material is based and derived from Evolving Zero Trust – Microsoft Position Paper.
Download the Basic – https://cybergeeks.cloud/wp-content/uploads/2023/03/Zero-Trust-Maturity_Basic.pdf
Download the Advanced – https://cybergeeks.cloud/wp-content/uploads/2023/03/Zero-Trust-Maturity_Advanced.pdf
Download the Optimal – https://cybergeeks.cloud/wp-content/uploads/2023/03/Zero-Trust-Maturity_Optimal.pdf