Monitoring Generative AI apps- Defender for Cloud Apps + MDE

Welcome back to the blog, it’s been a while! Today, we’re diving into a hot topic: how to use Defender for Cloud Apps and MDE to monitor and block Generative AI apps. With AI becoming more integrated into our workflows, it’s crucial to ensure these powerful applications are used safely and responsibly. I’ll guide you through setting up monitoring and blocking access where necessary to protect your organization. Let’s get into the details and boost your cloud security together!
As part of Microsoft’s XDR strategy, Microsoft Defender for Cloud Apps and Microsoft Defender for Endpoint integrate seamlessly to enhance security. In this example, I will mark an application as Unsanctioned on the Defender for Cloud Apps side and, because I have the integration with MDE, it will then block the app on the endpoint.
Enable MDA/MDE integration
First, to enable the integration between Defender for Cloud Apps and MDE go to Settings > Endpoint > Advanced Features and turn on Microsoft Defender for Cloud Apps.
Prerequisites
- Defender for Cloud Apps (E5, AAD-P1m CAS-D) and Microsoft Defender for Endpoint Plan 2, with endpoints onboarded to Defender for Endpoint
- Microsoft 365 E5
Microsoft Defender Antivirus
- Real-time protection enabled
- Cloud-delivered protection enabled
- Network protection enabled and configured to block mode
Operating systems
- Windows: Windows versions 10 18.09 (RS5) OS Build 1776.3, 11, and higher
- Android: minimum version 8.0: For more information see: Microsoft Defender for Endpoint on Android
- iOS: minimum version 14.0: For more information see: Microsoft Defender for Endpoint on iOS
- macOS: minimum version 11: For more information see: Network protection for macOS
- Linux system requirements: For more information see: Network protection for Linux
Other prerequisites
- Microsoft Defender for Endpoint onboarded. For more information, see Onboard Defender for Cloud Apps with Defender for Endpoint.
- Administrator access to make changes in Defender for Cloud Apps.
To enable cloud app blocking with Defender for Endpoint, please check: https://learn.microsoft.com/en-us/defender-cloud-apps/mde-govern#enable-cloud-app-blocking-with-defender-for-endpoint
Cloud app catalog
If you go to the Security Portal – https://security.microsoft.com – on the Cloud app catalog, you will see that we have Generative AI as a category. Once you’ve reviewed the list of discovered apps in your environment, you can enhance security by approving trusted apps (Sanctioned) or blocking unwanted ones (Unsanctioned) using the following methods.
Let’s use the following GenAI cloud app below as an example. It’s just an example, so I chose one of the first ones I saw in my lab environment.
We know that it’s quite common for users to ignore OAuth app permissions warning messages when accessing or using cloud applications and add-ons, often clicking ‘Accept’ on the permission request. As a result, they might inadvertently grant risky permissions to apps.
The good news is, you can review the connected apps when managing OAuth permissions in Defender for Cloud Apps. If you want to know more, please visit: https://learn.microsoft.com/en-us/defender-cloud-apps/manage-app-permissions.
Managing OAuth apps
Below, you can see that my user has added this app and accepted the OAuth permissions.
If you expand the details you will see more information about the app.
From here, one of the first things you can do if you want to block access to this application is to select ‘Mark app as banned‘.
After that, you will see the following red icon.
Right now, we are managing the OAuth app permissions. I also want to block access to this app so that Defender for Cloud Apps can inform MDE that it is a risky application.
Now, I’ll open the Cloud app catalog, select the app and tag it as Unsanctioned.
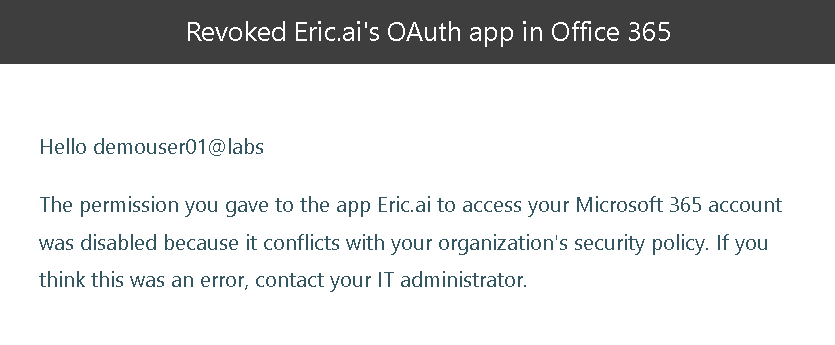
The user will receive an email explaining that the app has been revoked.
Also, if they try to open the page to access the cloud app, MDE will block access, and they won’t be able to access it again.
Tips
Below are some tips on what to check when monitoring cloud apps with Defender for Cloud Apps. Verify the general information and security features, such as auditing capabilities and whether MFA is supported. The compliance section is also very important; you can check if the app was developed according to best practices and strong standards.
You can also filter the cloud apps by the Risk Score and identify those that you could proactively block to prevent users from connecting to risky applications.
Policies
In addition to that, you can create policies. In the example below, I am using the Shadow IT category to alert when GenAI apps are discovered.
There are governance actions that help you take measures such as marking the app as unsanctioned or adding a tag to the application.
Purview / Compliance
It is important to mention that you can also leverage Microsoft Purview to prevent data leak through web apps with Microsoft Purview Data Loss Prevention. With that, you can establish policies to block users from copying sensitive data onto certain websites. This includes personal email platforms, generative AI prompts, social media, and others when they are accessed via a supported web browser. It accommodates both built-in and custom sensitive information types as defined by Microsoft Purview Information Protection.
Microsoft Purview DLP seamlessly integrates with Microsoft Edge across both Windows and macOS platforms. Additionally, its DLP capabilities can be expanded to include Chrome and Firefox through the Microsoft Purview extension.
If you want to know more about it, check out the following Microsoft Blog Post: Prevent data leak through web apps with Microsoft Purview Data Loss Prevention – Microsoft Community Hub.
If you want to learn more about how Purview can also help you with additional scenarios, check the following links:
Protect data used in prompts with common AI apps | Microsoft Purview
https://techcommunity.microsoft.com/t5/microsoft-mechanics-blog/protect-data-used-in-prompts-with-common-ai-apps-microsoft/ba-p/4085973
Check the integration between Purview DLP and MDE to prevent transfers from your company to GenAI apps.
https://learn.microsoft.com/en-us/purview/endpoint-dlp-using?tabs=compliance#scenario-5-restrict-unintentional-sharing-to-unallowed-cloud-apps-and-services
eBook: Data Loss Prevention: From on-premises to cloud
Thanks for reading!

