Microsoft Sentinel – Overview
Level: Beginner | Reading time: 10 minutes
In this article, I will present an overview of Microsoft Sentinel, Microsoft’s cloud SIEM.
Intro
Microsoft Sentinel emerged as a SIEM (Security information and event management) and SOAR (Security Orchestration, Automation, and Response) cloud solution sold as a service. This makes it much easier not only to deploy this type of service but also to manage the entire solution, you don’t need to worry about all the infrastructure that would run in your data center and focus on configuring the solution’s intelligence.
This is very important nowadays for managing a modern SOC. Typically, SOC analysts have to manage a huge amount of incidents and alerts they receive and often some alerts that could be avoided or automated. Freeing the SOC team from the well-known “alert fatigue” makes your incident response team focused on what really matters, bringing more intelligence to monitor and manage information security events.
What is the Microsoft Sentinel?
As explained in the introduction above, we can highlight that Microsoft Sentinel works as a security event and information management (SIEM) and also security orchestration automated response (SOAR). This enables us to achieve intelligent security analytics and threat intelligence across the organization, providing a single solution for alert detection, visibility, proactive search and threat response.
The image below, taken from Microsoft docs, illustrates well the main features of Microsoft Sentinel.
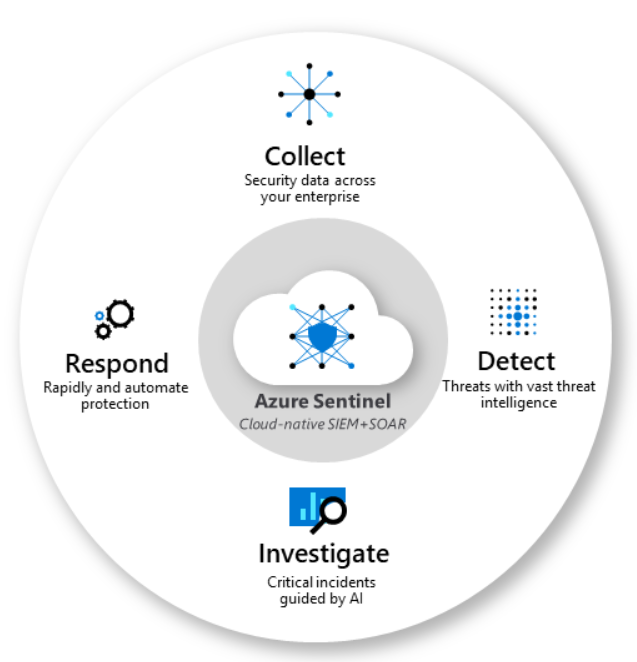
We can highlight the main features below:
- Collection of data from users, devices, applications and infrastructure, in on-premises and/or multi-cloud environments.
- Detection of undiscovered threats, minimizing false positives using Microsoft threat analysis and intelligence, called Microsoft Intelligent Security Graph, which offers, also as a SaaS, about 9 trillion daily signals for the clients.
- AI threat investigation and suspicious activity at scale.
- Quickly respond to incidents with orchestration and automation (SOAR).
Today, a challenge that I see large companies facing is the number of alerts and the management of the on-premises SIEM infrastructure, and often the lack of ease of integration with other solutions and with the cloud itself. Sentinel works with connectors that make integration much easier and has a pre-registered list where, sometimes just by clicking enable, you can easily bring events into Microsoft Sentinel.
But before you start ingesting events, you need to define and estimate storage. Despite being a SaaS service, there are parts of the configuration that you need to define and a very important one is regarding the storage of logs. I will leave the details for later articles, but it is worth explaining here that this is done by writing the logs to the Azure service called Log Analytics, and therefore, one of the prerequisites for you to start using Microsoft Sentinel is to configure the Log Analytics. A Workspace, Log Analytics workspace, is a unique environment for Azure Monitor log data. Each workspace has its own data store and configuration, and you need a Log Analytics workspace if you intend to collect data for use by Microsoft Sentinel.
A very important initial planning task is to define the volumetry and estimate the costs of services so that they are in accordance with the needs of the organization. Microsoft Sentinel is billed based on the volume of data ingested for analysis and stored in the Azure Monitor Log Analytics workspace. Microsoft Sentinel offers a predictable and flexible pricing model. There are two ways to pay for the service: Capacity Reservations and Pay-As-You-Go.
On the Microsoft Sentinel settings page itself, you can see the pricing table:
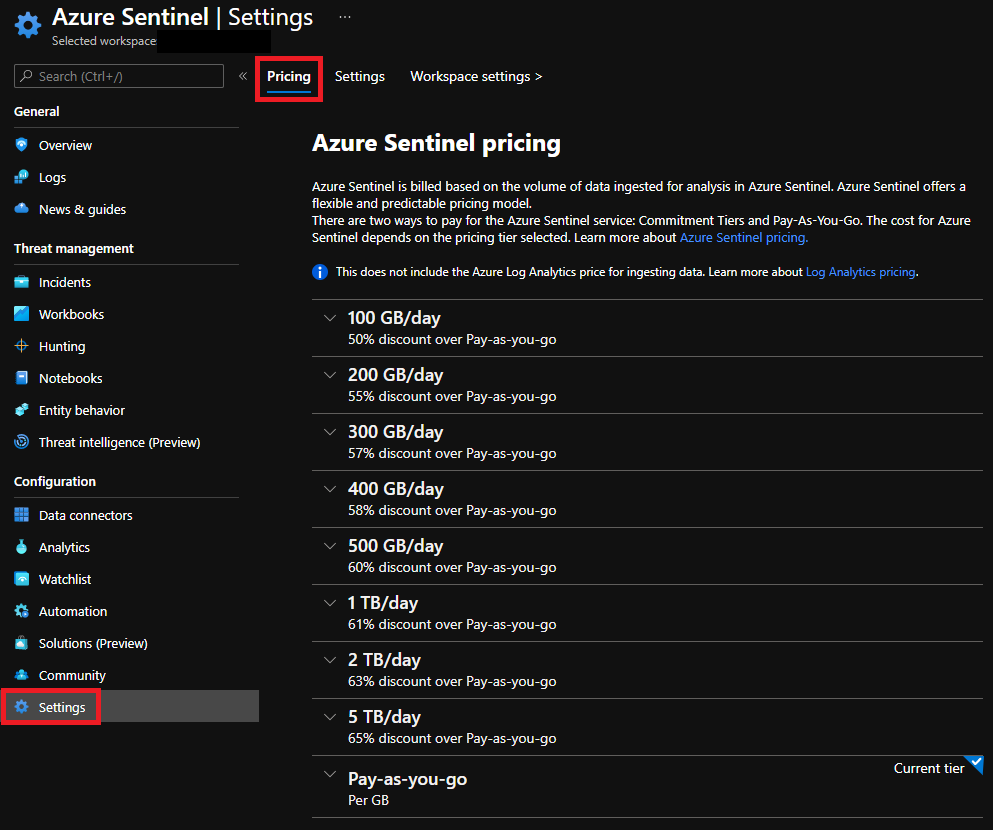
At this early stage, you will also need to define your long-term log storage needs. If your company has any need to retain data for compliance reasons, you will have to define the best structure for this. I recommend reading this blog to check the available options. Further pricing details can be viewed on the following website.
With Log analytics configured, it is very simple to add data through the connectors. So this is going to be one of the first tasks you will do after starting the Microsoft Sentinel configuration.
Sentinel can be accessed from the Azure Portal at: https://portal.azure.com. Once logged in, just search for Sentinel in the search bar:
Here we can see our settings menu and the Data Connectors menu:
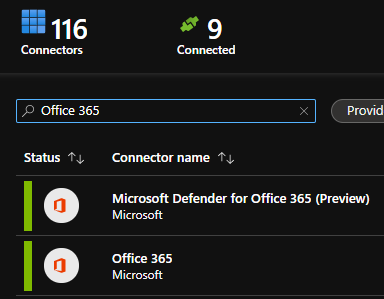
When I search for Office 365 I already have a pre-configured connector for use:
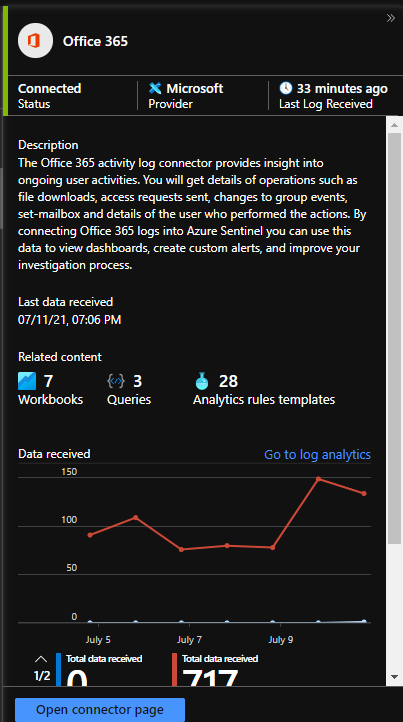
In my example above it is already connected to Sentinel and receiving the logs, so it is marked in green. But by clicking on it we can open the connector page on the right side:
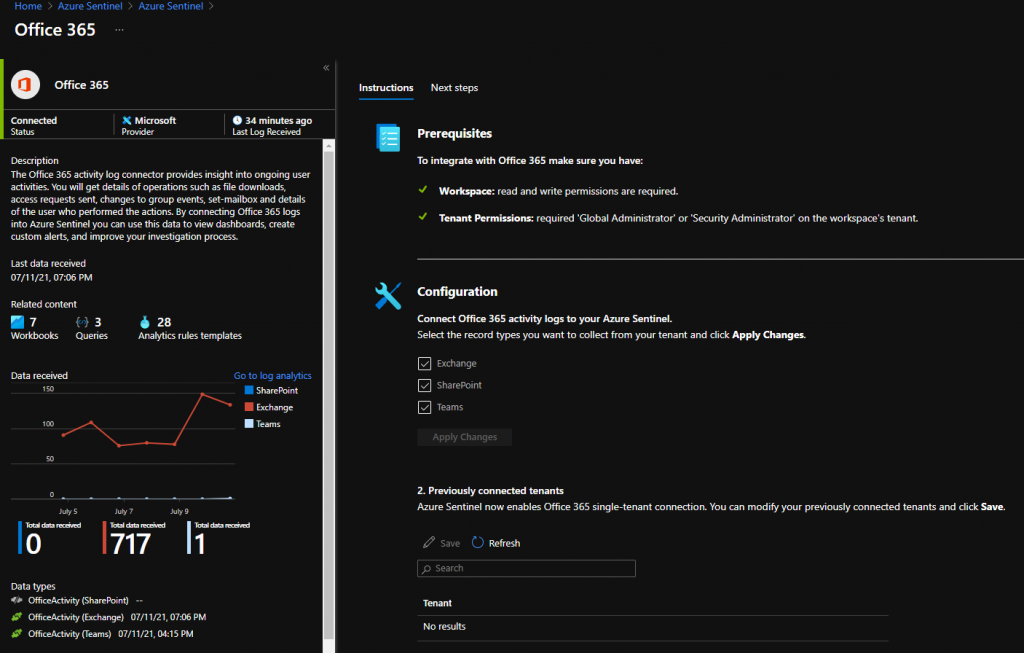
It’s very simple in the case of Office 365, for example, being inside the connector page, you can choose which applications you want to receive alerts by selecting Apply changes:
Once the data is connected, Microsoft Sentinel also offers the following important settings.
- Workbooks – Can help you to create interactive and personalized reports on your data and also already have built-in templates so you can quickly get insights into your data as soon as you connect a source.
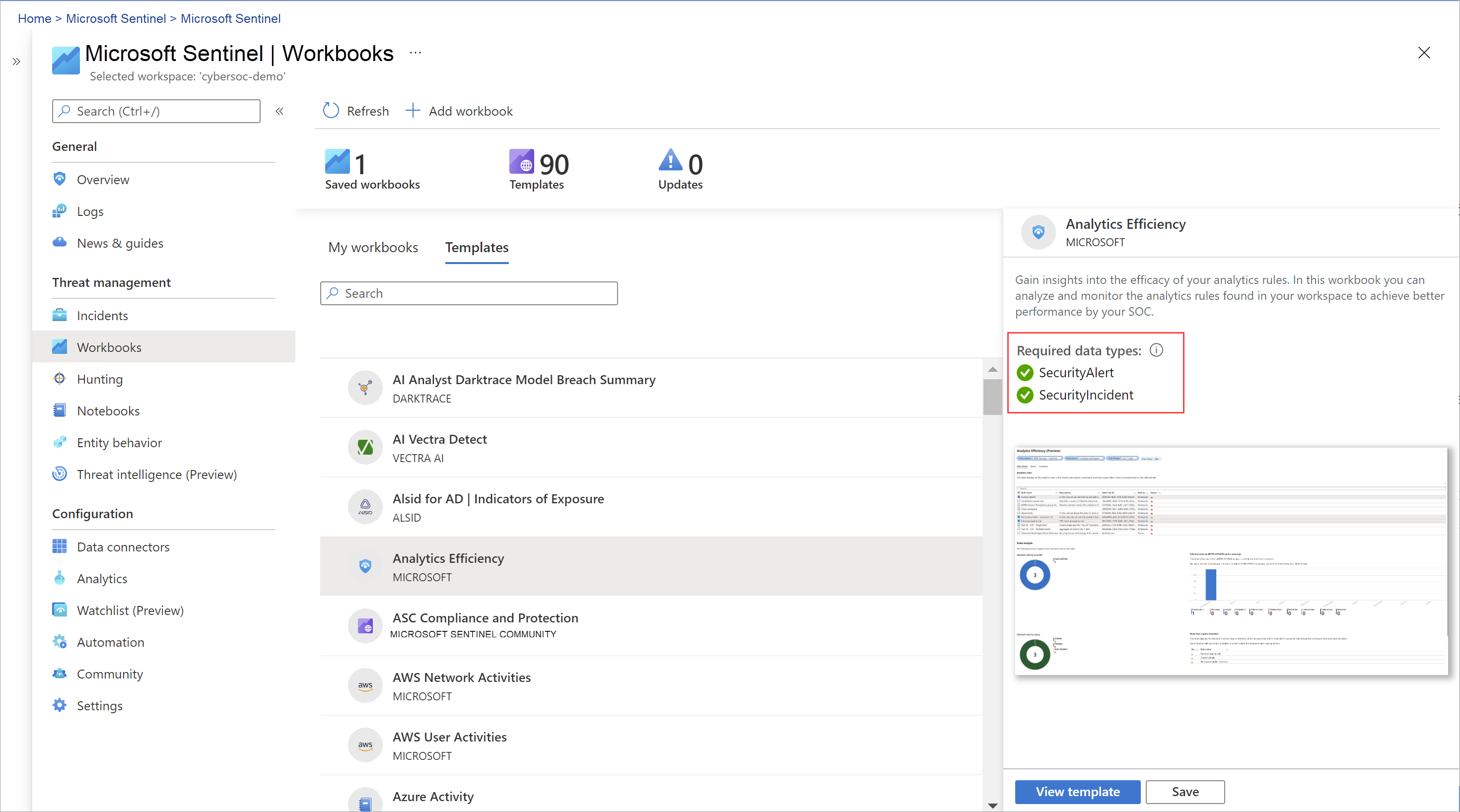
- Analytics – Sentinel uses analytics to correlate alerts to incidents and also provides machine learning rules to map network behavior and then look for anomalies across all your resources. These analytics connect the dots as they combine low-fidelity alerts about different entities into potential high-fidelity security incidents.
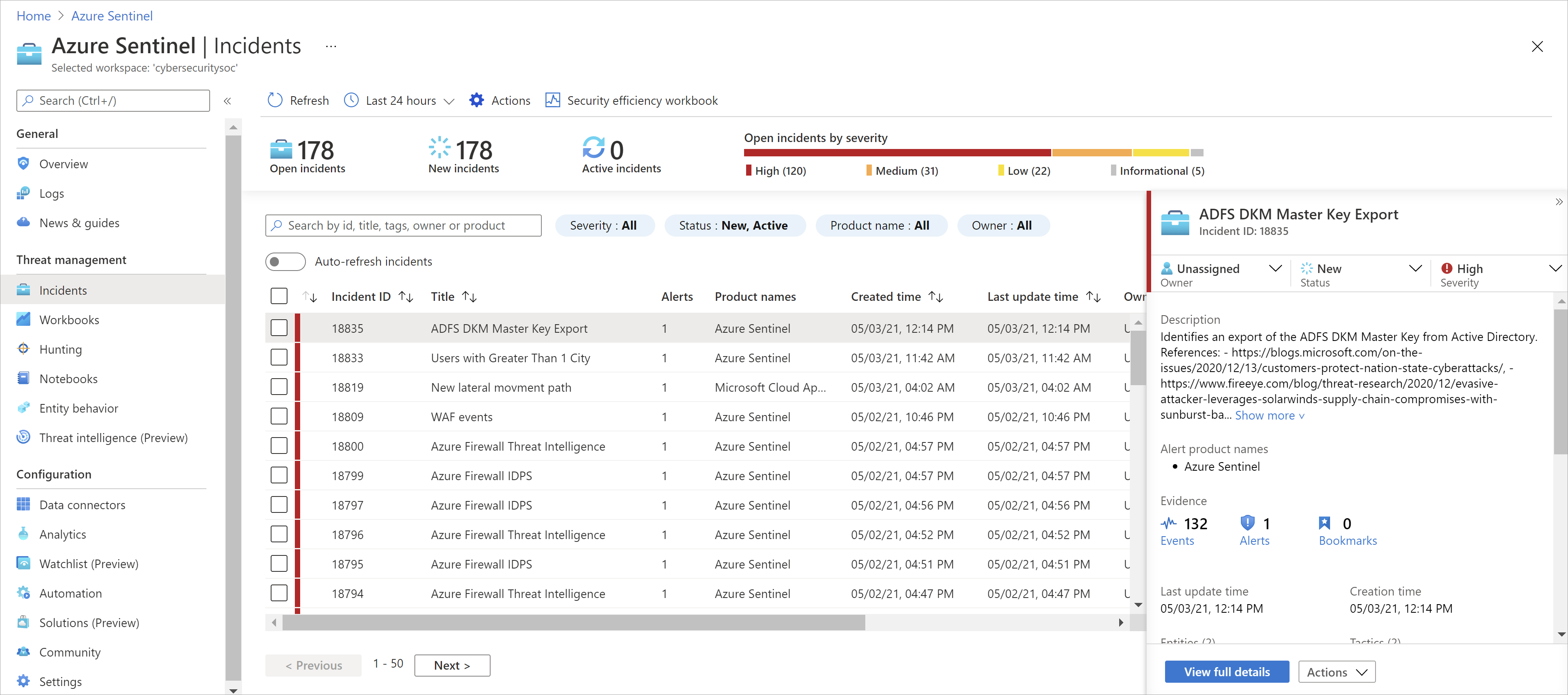
- Playbooks (Automation) – Automation rules allow you to centrally manage all incident handling automation. It simplifies the use of automation in Microsoft Sentinel and your complex workflows for your incident orchestration processes. Rules are triggered by incident creation. You can define conditions to control when actions will be performed, based on incident and entity details and analysis rules. You can also set the action order and rule expiration time.

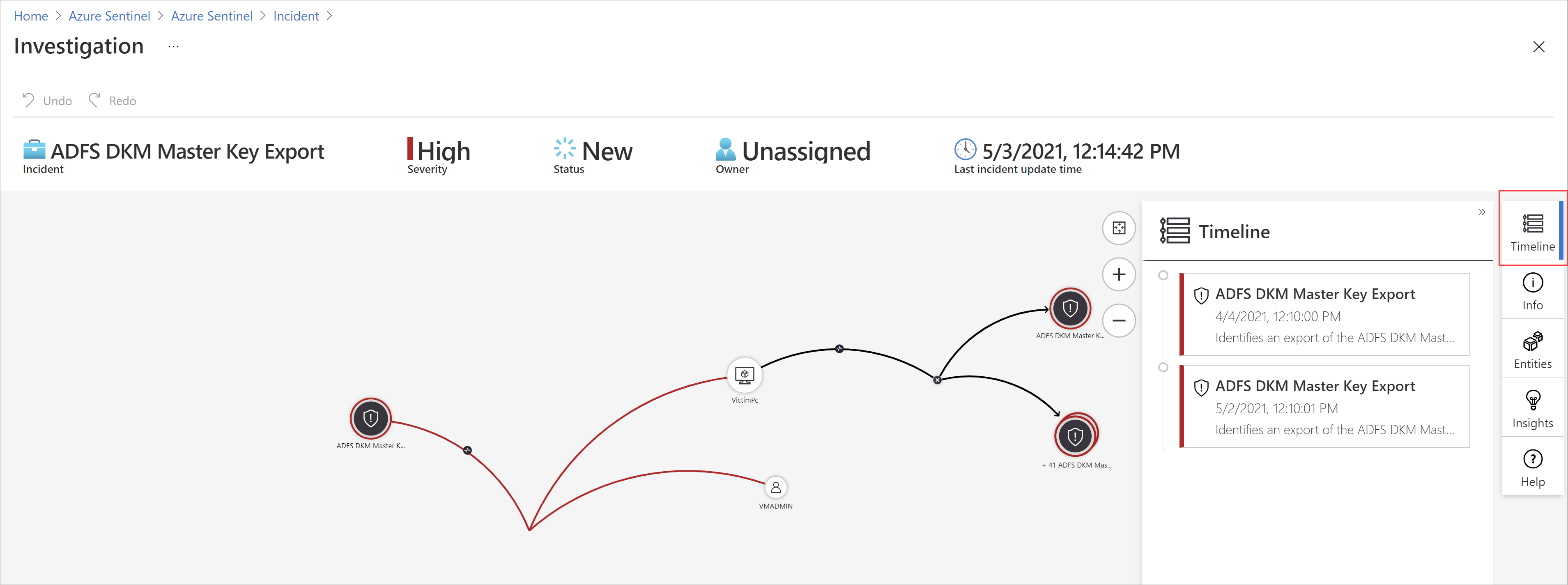
- Investigation (preview) – Investigation (preview) – Microsoft Sentinel’s deep investigation tools help you understand the scope and find the root cause of a potential threat.
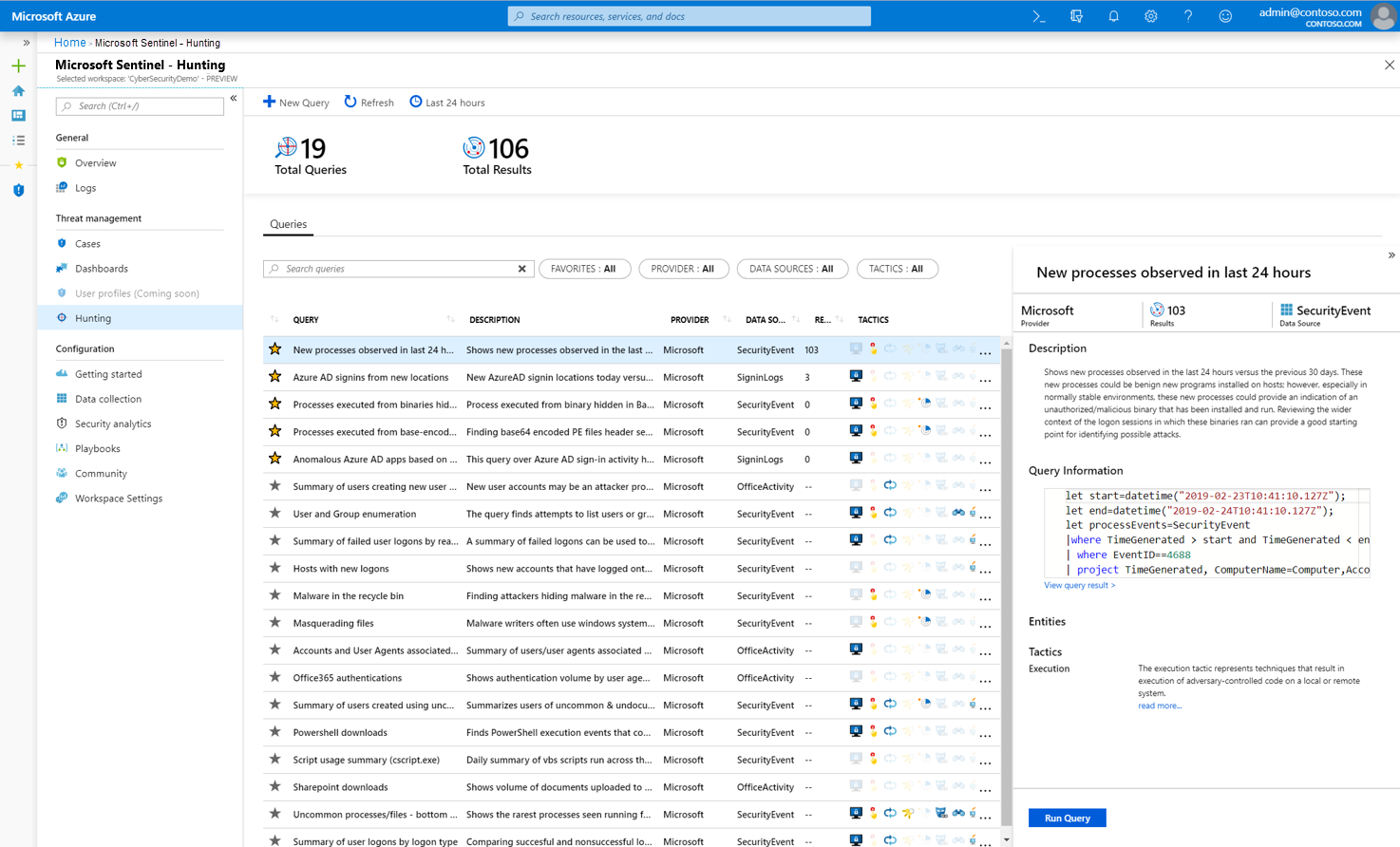
- Hunting – Based on the MITER ATT&CK framework, you can proactively search for security threats in your organization’s data sources before an alert is triggered.
- Community – The Microsoft Sentinel community is a resource for threat detection and automation. Microsoft security analysts constantly create and add new workbooks, playbooks, search queries, and more, publishing them to the community for use in your environment. You can download sample content from the GitHub repository.
Conclusion
In this article, I showed an initial overview of Microsoft Sentinel. To learn more about this tool, visit the links below:
What is the Microsoft Sentinel? | Microsoft Docs
Want to know how to start from scratch? Consult the guide Quick-Start Guide: Microsoft Sentinel | Microsoft Docs.