Microsoft Sentinel Threat Intelligence – Part I – Overview

Microsoft Sentinel is a cloud-based Security Information and Event Management (SIEM) solution and a Security orchestration, automation, and response (SOAR) platform. In this post, I will explore the possibilities of leveraging cyber threat intelligence (CTI) feeds on Sentinel so that you can use the threat indicators, also known as Indicators of Compromise or IoCs, to detect, provide context, and respond to existing or potential cyber threats.
But first, as Theat Intelligence can have different explanations for different people, let’s start with the basics from Wikipedia and Gartner for us to be on the same page.
What is a Threat Intelligence Platform (TIP)?
To start explaining why Threat Intelligence is important in the Microsoft Sentinel platform, I am going to start with an overview of it with the help of Wikipedia:
Threat Intelligence Platform is an emerging technology discipline that helps organizations aggregate, correlate, and analyze threat data from multiple sources in real time to support defensive actions. TIPs have evolved to address the growing amount of data generated by a variety of internal and external resources (such as system logs and threat intelligence feeds) and help security teams identify the threats that are relevant to their organization. By importing threat data from multiple sources and formats, correlating that data, and then exporting it into an organization’s existing security systems or ticketing systems, a TIP automates proactive threat management and mitigation. A true TIP differs from typical enterprise security products in that it is a system that can be programmed by outside developers, in particular, users of the platform. TIPs can also use APIs to gather data to generate configuration analysis, Whois information, reverse IP lookup, website content analysis, name servers, and SSL certificates.
Gartner’s definition:
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications, and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.
Therefore, to be prepared to tackle modern cyber-attacks, stay ahead of the curve against attackers, and provide your SOC with the right signals to automate operations, it’s essential to have a bunch of TI indicators to help you.
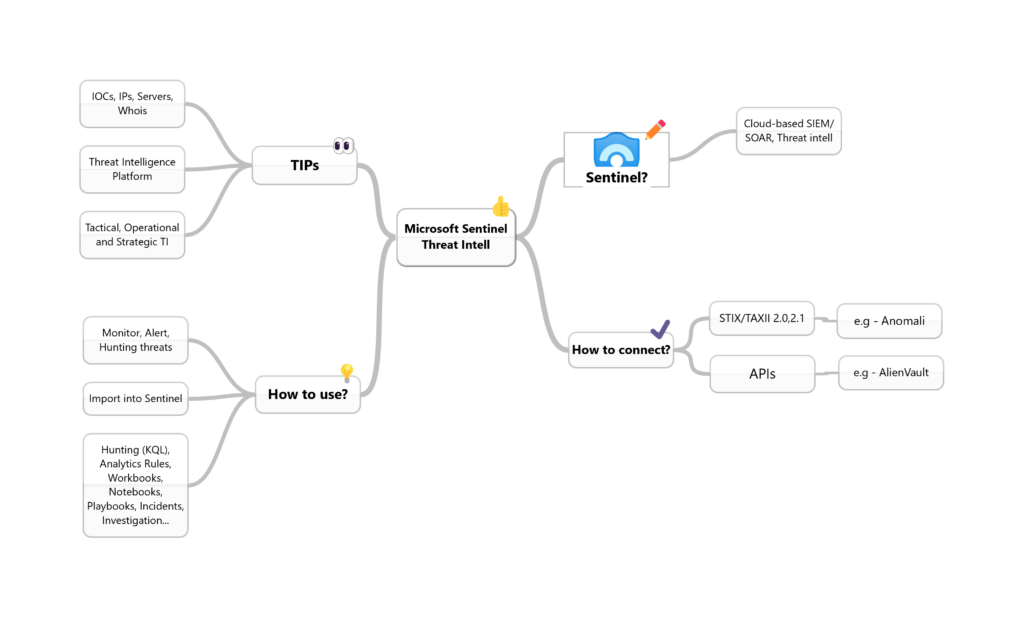
How does Microsoft Sentinel leverage TIP?
You can leverage CTI feeds to have an extra context to unusual activity so that your SOC personnel can quickly take action to protect assets. The most common indicators contain information such as URLs, hashes, IP addresses, domain names, and they are often called tactical threat intelligence and are more frequently used with SIEMs like Sentinel. We also have the Operational TI, which verifies information like the threat actor names and provides a rich contextual TI, and Strategic TI, more relevant to understanding the motivations and intentions of an attacker group like a nation-state APT or that focuses on a particular type of industry.
You have some options to connect CTI sources from many places; for example, you can use open-source data feeds, threat intelligence-sharing communities, paid intelligence feeds, and local intelligence gathered during security investigations within an organization.
You can import these indicators into Sentinel using data connectors. The most common ways to connect threat intelligence sources to Microsoft Sentinel are:
- “Threat Intelligence – STIX/TAXII version (2.0 or 2.1)” using server URI & collection ID
- “Threat Intelligence Platforms” using the Microsoft Graph Security API
In my other article, I showed how to integrate Alien Vault OTX Threat Indicators into Microsoft Sentinel for you to implement in your lab.
The easiest way is to use TAXII connector, but sometimes your organization wants to use other threat intelligence platforms (TIP) that don’t support STIX/TAXII protocols, so that you can use APIs, for example. The TIP data connector works with the Microsoft Graph Security tiIndicators API to accomplish this,
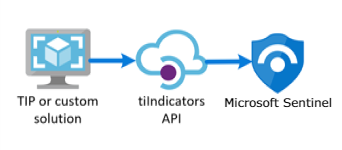
STIX/TAXII definition, according to Anomali - STIX and TAXII are standards developed in an effort to improve the prevention and mitigation of cyber-attacks. STIX states the “what” of threat intelligence, while TAXII defines “how” that information is relayed. Unlike previous methods of sharing, STIX and TAXII are machine-readable and therefore easily automated.
Let’s have a look at the Data Connectors and its description on the Sentinel portal:
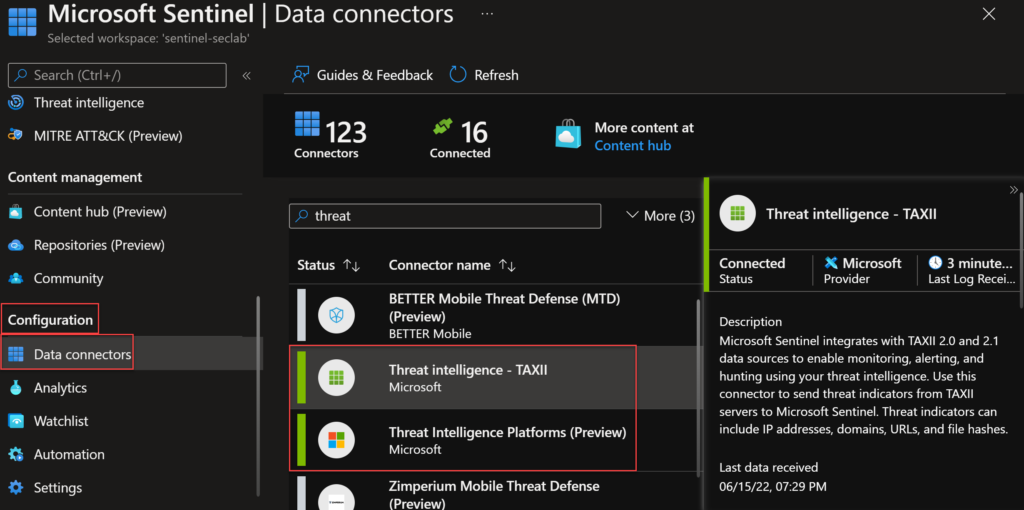
Threat intelligence – TAXII – Microsoft Sentinel integrates with TAXII 2.0 and 2.1 data sources to enable monitoring, alerting, and hunting using your threat intelligence. Use this connector to send threat indicators from TAXII servers to Microsoft Sentinel. Threat indicators can include IP addresses, domains, URLs, and file hashes.
Threat Intelligence Platforms (Preview) – Microsoft Sentinel integrates with Microsoft Graph Security API data sources to enable monitoring, alerting, and hunting using your threat intelligence. Use this connector to send threat indicators to Microsoft Sentinel from your Threat Intelligence Platform (TIP), such as Threat Connect, Palo Alto Networks MindMeld, MISP, or other integrated applications. Threat indicators can include IP addresses, domains, URLs, and file hashes.
How can I use these signals in Sentinel?
We have a bunch of use cases for these threat intelligence feeds. After importing TI data into Sentinel, you can use it in various parts of the product like hunting, investigation, analytics, workbook etc.
The Microsoft Sentinel official blog has some examples of use cases for this, and I plan to cover some of these cases here in the blog, such as:
Import Pulsedive Feed into Microsoft Sentinel – Microsoft Tech Community
Bring Threat Intelligence from SEKOIA.IO using TAXII data connector – Microsoft Tech Community
I will leave here an excellent video from Microsoft Security channel showing how to use Threat Intelligence to detect malicious activity in Microsoft Sentinel:
Conclusion
In this first part, I showed you what threat intelligence is, how Microsoft Sentinel integrates with external feeds, and some use cases. In future posts, I will show you how to connect a TAXII server to Microsoft Sentinel, focusing on the built-in TAXII connector and configuring Anomali as a TI feed. If you want to check the API method, you can read my previous article here.
Thank you!