Microsoft Sentinel Threat Intelligence – Part II – View and manage your threat indicators

In the first part of this series, I showed what threat intelligence is, how Microsoft Sentinel integrates with external feeds, and some use cases. Today, I want to cover how you can view and manage your threat indicators on the Microsoft Sentinel portal.
Threat Intelligence Indicator Table (KQL)
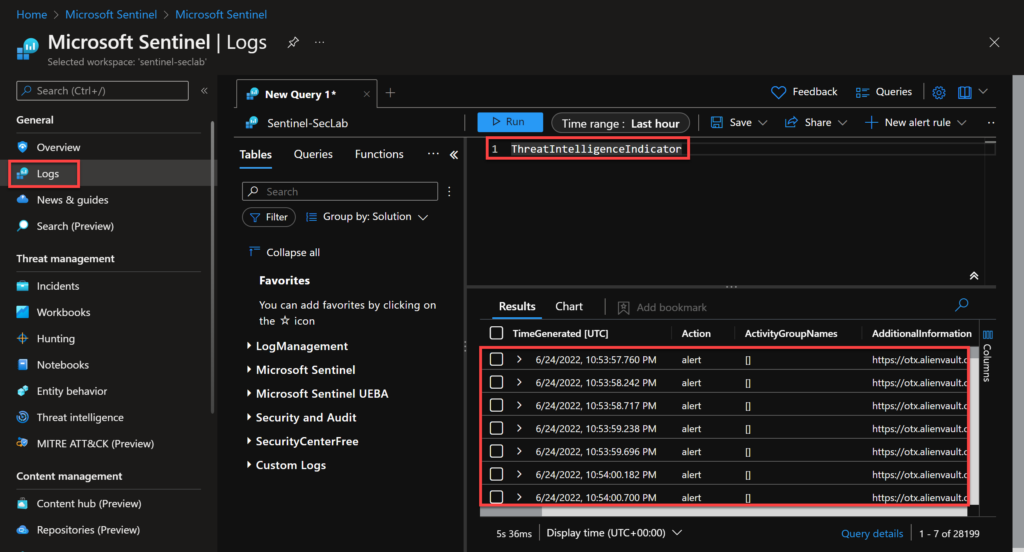
If you are wondering – where is my threat intelligence feed stored? It’s easy to figure it out. When importing your threat intelligence source, the data will be recorded into a log analytics table called ThreatIntelligenceIndicator. So, we just need to go to the Logs section on the Sentinel portal and run a KQL (Kusto Query Language) query. Other Sentinel components we will cover soon, such as Analytics and Workbooks, use the same table to retrieve TI data.
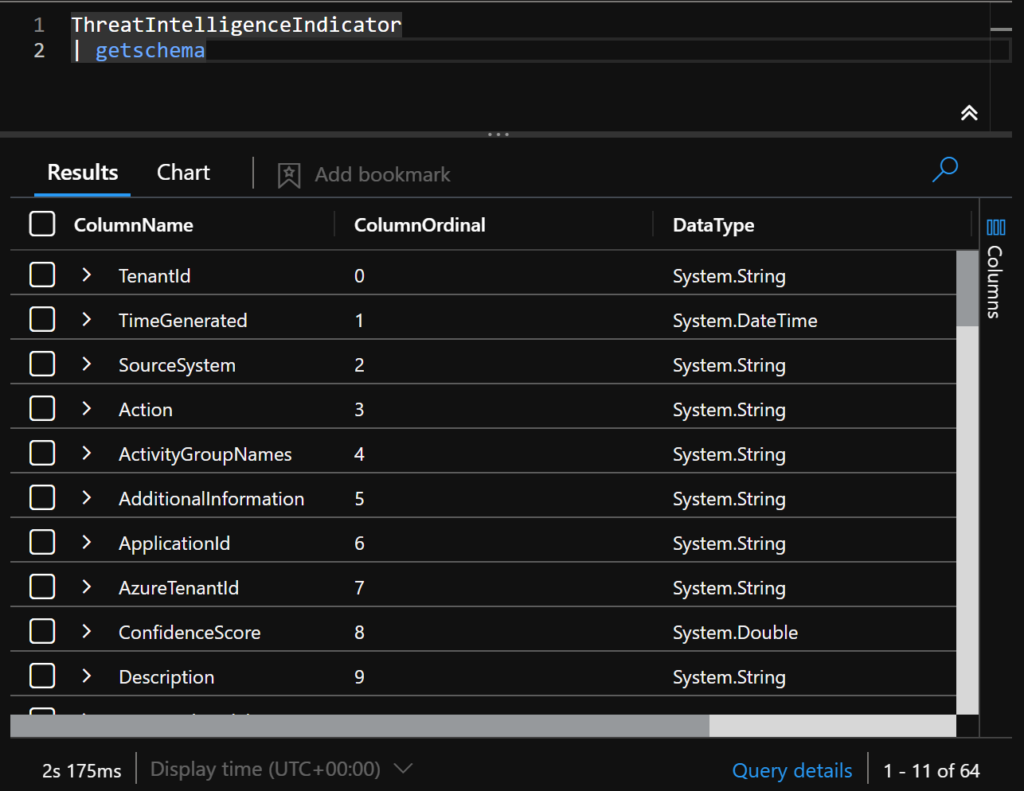
You can just type ThreatIntelligenceIndicator to look for all the results in the table.
Tip: You can see other examples in the Sentinel GitHub community.
To better understand the schema of this table, you can run:
ThreatIntelligenceIndicator
| getschema
Microsoft Sentinel Threat intelligence menu
The other way to view and manage indicators is more visual. You can go to the Sentinel portal and select: Threat Management > Threat Intelligence.
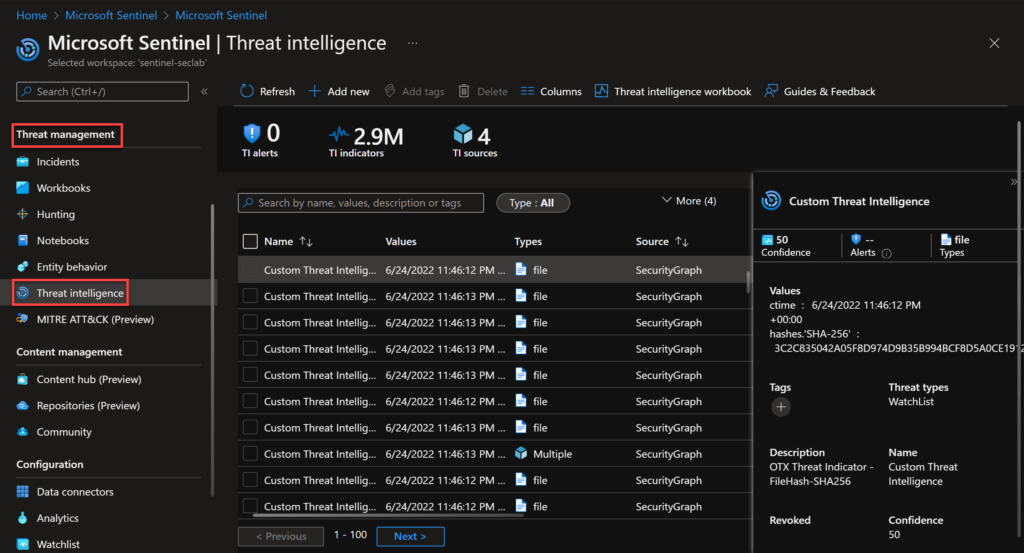
In this page we can:
- Add/Delete a new indicator manually
- Access the Threat Intelligence workbook (I’ll cover this in some next post)
- See the metadata of the selected IOC
- Tag indicators
- Filter the list of the IOC’s based on a specific parameter
I find tags especially useful. With that, you can apply a tag to indicators related to an incident or if you are investigating a particular attack campaign. I suggest you create naming conventions and standards for those tags to make them easier to use during an investigation.
So, let’s add a new indicator manually to test. We have the following types to add: domain name, file, ipv4, ipv6 and url.
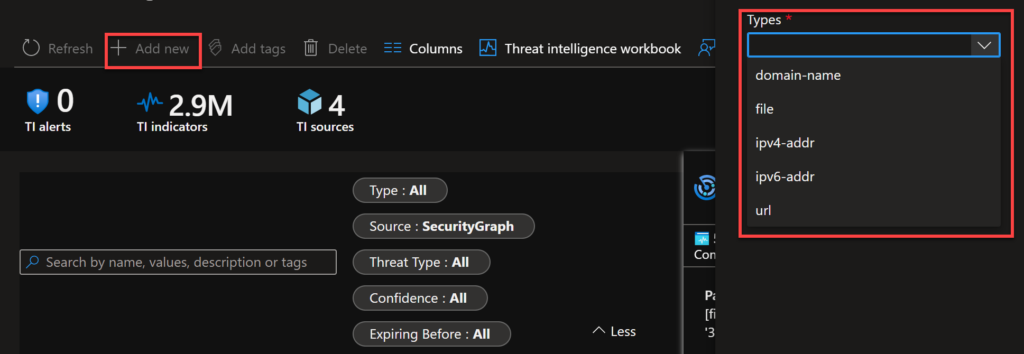
As it’s just a lab, I am creating the http://attacker.com URL. You can also add tags, the threat types and the description here.
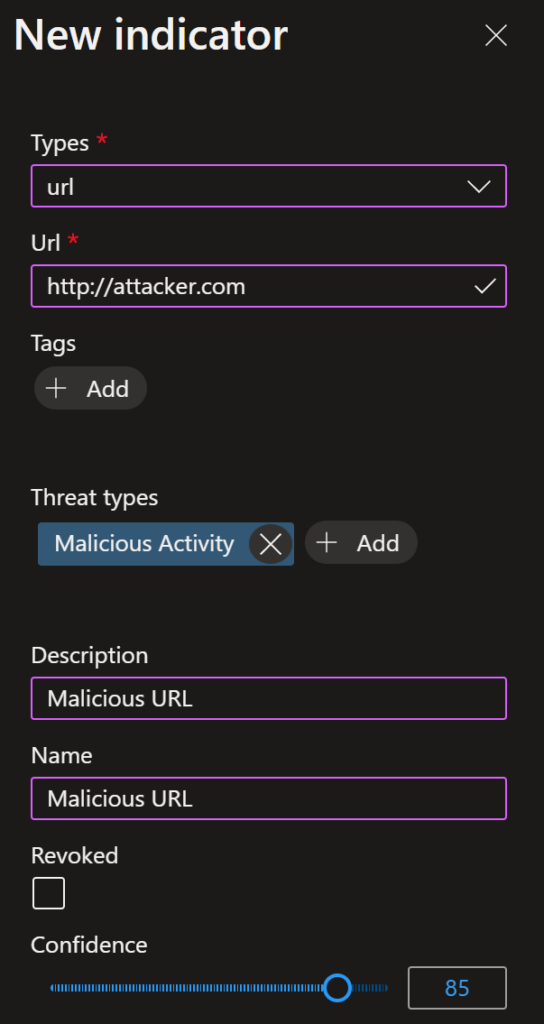
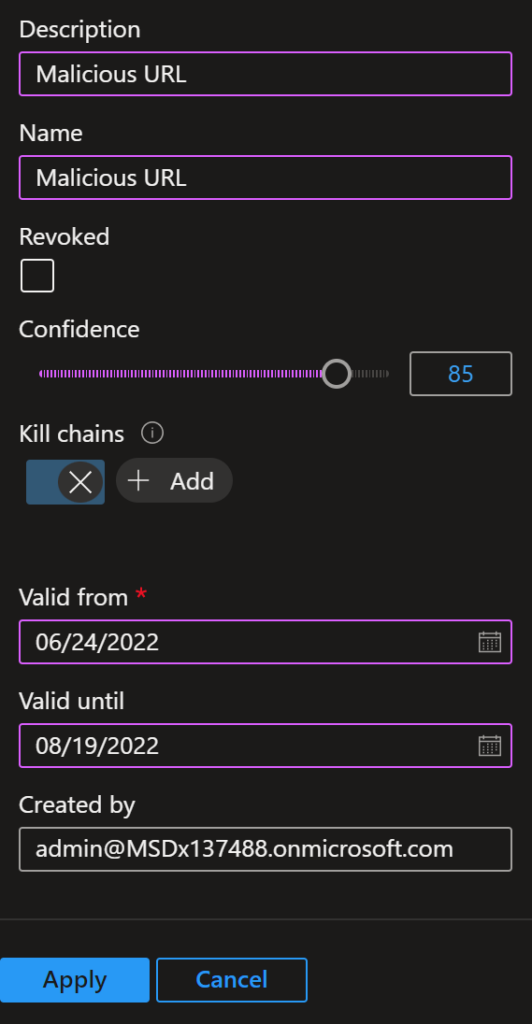
I can also add the confidence, kill chain information and how long this will be valid.
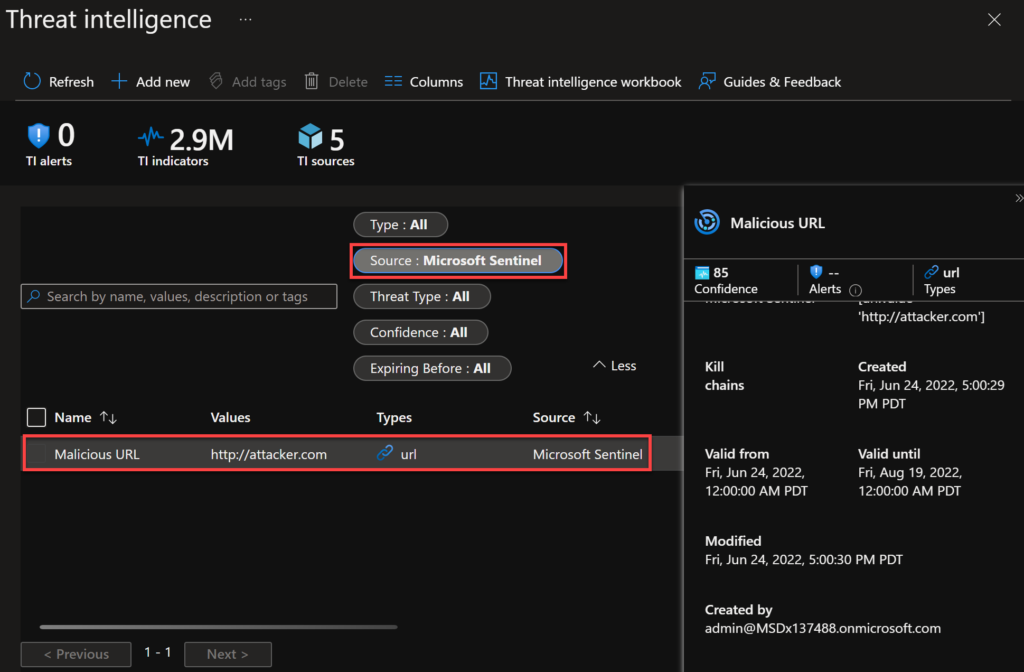
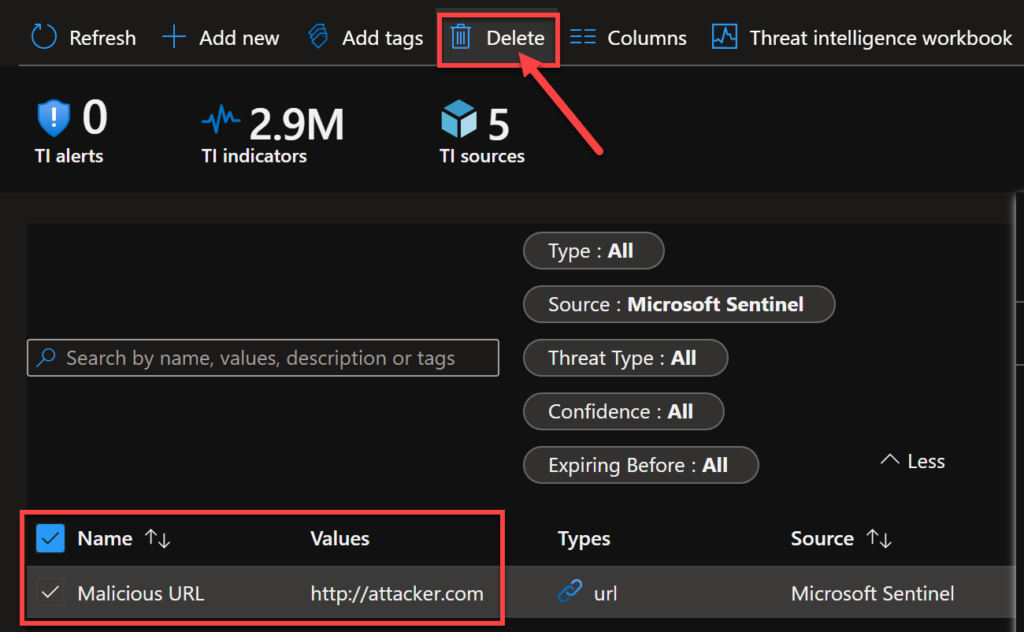
After applying, I can see my indicator on the Threat Intelligence menu. If you have more types, it’s easier to find filtering by Source: Microsoft Sentinel.
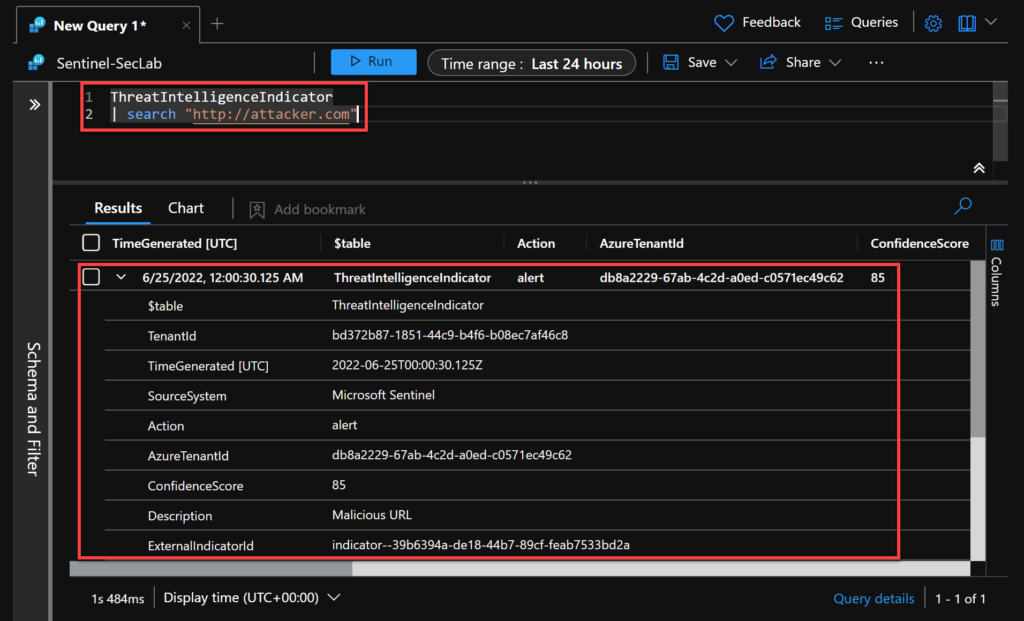
As this is being recorded in the same table, we can use KQL to query our new indicator.
If you want to delete it, you just need to select the manual IOC and select Delete.
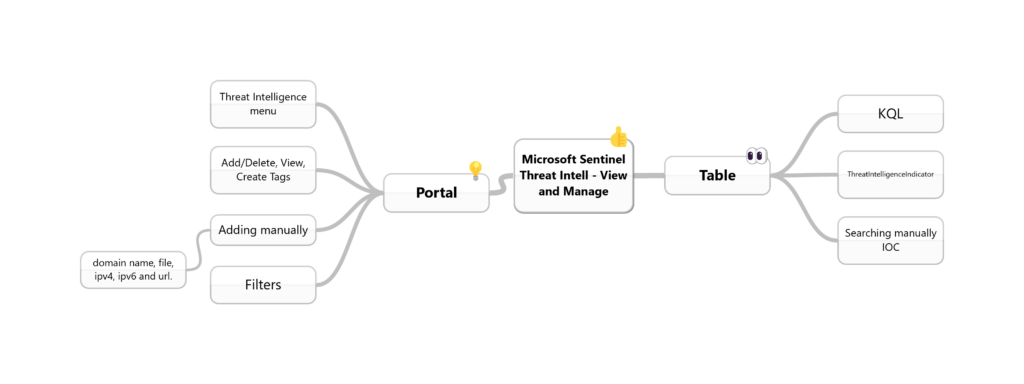
To conclude, I’ll add a mind map for us to remember the most important topics from this post.
Reference
Work with threat indicators in Microsoft Sentinel | Microsoft Docs
Summary
I covered today how to view and manage your threat indicators using the log analytic table and the Threat Intelligence menu on Sentinel.